

Are CISOs Ready to Face Shadow AI Risks?
With these predictions becoming dreaded headlines for many organizations worldwide, it is indeed a matter of concern as artificial intelligence takes a massive leap. Transforming and revolutionizing enterprise operations big time, artificial intelligence has become the bone of contention for Chief Information Security Officers (CISOs). It is a proven record that the world has witnessed a widespread impact of AI on organizational security; that has led to gruesome losses and reputational damages. Going forward;

With regulatory compliance continuing to become a challenge, and AI-powered attacks increasing threat levels; it is time CISOs looked into a way out of this menace. Establishing an AI governance program, focusing on Shadow AI, preparing for increased security audits, and considering strategic outsourcing are active measures to be deployed to secure the situation. Among these, Shadow AI remains a significant concern for CISOs. This read shall focus on this very concept, with diving deeper into the associated risks, ways to spot and safeguard against them, and devising a safety plan for organizations.
Early Ruins- Shadow AI
It all began with bring your own device (BYOD) and cloud technology; where employees move faster than their corporate leaders and introduce tools into the workplace without the oversight of IT teams. Shadow AI is a byproduct of artificial intelligence’s accessibility and democratization; reflecting the growing role of technology in modern workflows. Unregulated and unauthorized use of AI is redefining what enterprise risks look like. Shadow AI can have many devastating repercussions if left unchecked. The further subsections are targeted at strengthening your understanding of every facet of Shadow AI and what the future would look like.
What is the Urgency?
Seeing the cat out of the box, still, there are many businesses and organizational leaders that question the need to address Shadow AI urgently. The CISOs play a critical role in building the guardrails for an organizational asset and attending to Shadow AI like an expert. The reasons could be many;
- Unauthorized AI tools may access sensitive data without proper security measures
- Regulatory compliance issues may arise if AI usage is not monitored nd controlled
- The misuse of AI can lead to data breaches, undermining trust, and damaging the organization’s reputation
- Unregulated AI tools can disrupt operations and lead to unexpected consequences
While you were reading these concerning trigger points, you must be reminded of recent and past events of attacks being faced by global industry giants such as Marks & Spencer (M&S) Retail Attack in the UK, leading to hundreds of millions of financial losses; Municipal Cyberattacks at the Grove city with data being compromised; Adidas customer data compromise via third-party security failures; among many other incidents.
Rise of Shadow AI- An Unseen Threat
CISOs face massive challenges while deploying artificial intelligence across their organization in the form of Shadow AI. This rapid proliferation of shadow AI is broadly allowed through unsanctioned AI tools used by employees without security oversight. This being the common reason of the burgeoning risk, shadow AI is a massive risk in the cloud era. From compliance risks to unintended data exposure; shadow AI can impact adversely in multiple ways. Enterprises need robust auditability, explainability, and red-teaming processes in place to evolve regulatory requisites.
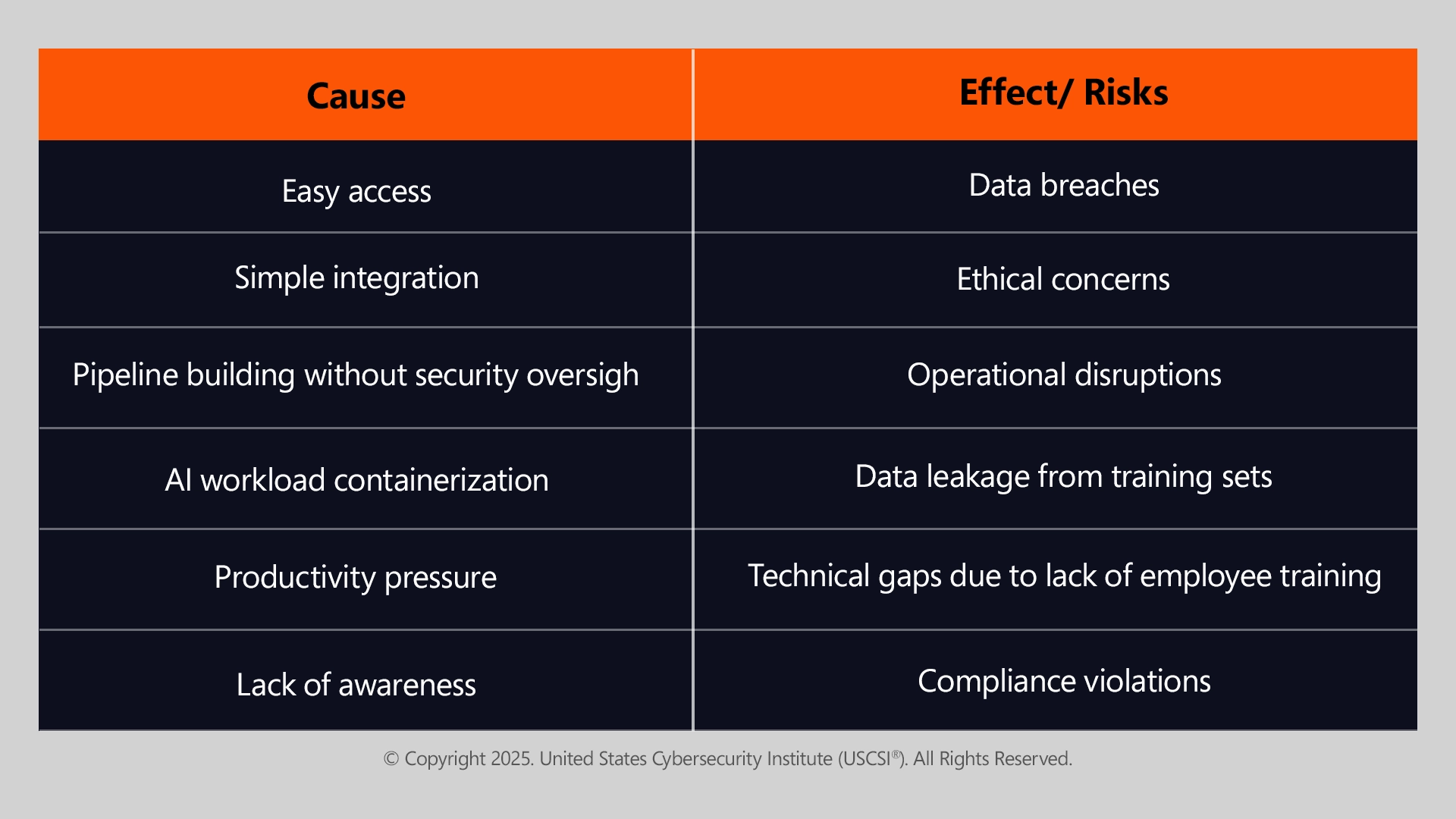
Cause and Effect- Shadow AI Risks
Seeing the Unseen- Risk Spotting
There are many ways that Shadow AI vigilance and proactive measures can be implanted. The foremost step is to train the employees with the trusted cybersecurity leadership certifications that are inclusive of key data loss prevention tools, generative AI, and other facets of industry-relevant upskilling. Risk spotting must involve conducting regular audits to detect unauthorized AI tools within the organization. Monitoring tools by implementing systems to track AI activity and usage patterns shall be of help. One thing must be ingrained in the organizational structure that no team can work in silos. It is an imperative aspect of higher-grade security to have cross-department collaboration; to work in sync and fight shadow AI and other security menace efficiently.
Taming Shadow AI- Mitigation Plan
-
Monitor AI Usage
Implementing monitoring tools can detect AI-related activities across networks, apps, and cloud services. They can also identify AI-related API calls to external services, ML libraries and frameworks, model files, data transfers to AI services, and vector databases and embedding services.
-
AI Tools Audit and Inventory
This forms the baseline for governance efforts. The inventory should include details on what AI systems are being used, by whom, for what purposes, and what data they process.
-
Defining Clear AI Policies
These policies must be inclusive of approved AI tools and platforms, data handling requisites and restrictions, compliance obligations, security and privacy standards, ethical guidelines for AI development and usage; and approval processes for new AI implementations.
-
AI Governance Technical Implementation
CI/CD pipeline integration, dependency governance, and network controls constitute the grounding foundation of AI governance tech implications.
-
Tech Guardrails and Access Controls
Proxy services for AI APIs, container security policies, AI development environment security, data loss prevention tools, container security policies, access control enforcement, enclave security for sensitive AI processing, and monitoring for unauthorized use of AI model hosting platforms must be taken into consideration.
-
Employee Education
Raising awareness about Shadow AI risks and offering requisite training and cybersecurity specialist certifications to the security personnel is a must to build a culture of anti-tolerance against Shadow AI.
-
Incident Response Planning
With robust protocols in place such as detection mechanisms, isolation procedures, unauthorized AI model or extension or container eradication, forensic analysis approaches, remediation steps, communication protocols, and postmortem analysis must be a part of the plan.
Questions to be Addressed!!
As the Chief Information Security Officer (CISO) of an organization; you must ask yourself the following question before devicing a security policy.
- Are employees educated about the damages of Shadow AI?
- What policies or governance are in place to prevent Shadow AI?
- Where might Shadow AI already be present in the business?
- Are we sufficiently monitoring or controlling network security activities?
Prepare for the Future
Targeting a safe future involves attending to the above listed question with an open mind and incorporate the suggestive containment plan to build a robust guard against Shadow AI. It shall not be limited to a one-day exercise. This shall involve a continuous understanding, reflection, and purpose-driven security measures in place. If you are someone who is planning on a cybersecurity career, please be mindful that it is nothing short of a ride that involves thrill, excitement, and way more zeal from your end to excel as the malicious threat actors never sleep, so should you! Plan wisely!





