

Preparing for Emerging Cybersecurity Threats 2026
Five years from now, cybersecurity won’t just be about safeguarding your passwords — it will also involve protecting entire AI ecosystems, virtual economies, and autonomous agents that act on their own in the world. As cyber defenses are evolving, so are the cybersecurity threats.
Did you know that 72% of GCO survey respondents reported a rise in cyber risks? (WEF Global Cybersecurity Outlook 2025)
As per Google Cloud’s Cybersecurity Forecast 2026, three dynamics are rewriting the global security landscape: the complete adoption of artificial intelligence by cyberattacks, escalating data-centric cybercrime, and a surge in nation-state digital conflicts.
The age of AI, cybersecurity is no longer merely a digital safeguarding skill, but a core of global cyber survival skills.
Evolving Cybersecurity Landscape
The line between physical and virtual worlds is blurring. Two decades from now, the machines could dominate all industries. These digital advancements will increase more ways to perform cyber attacks, and as technology is evolving, threats are also evolving.
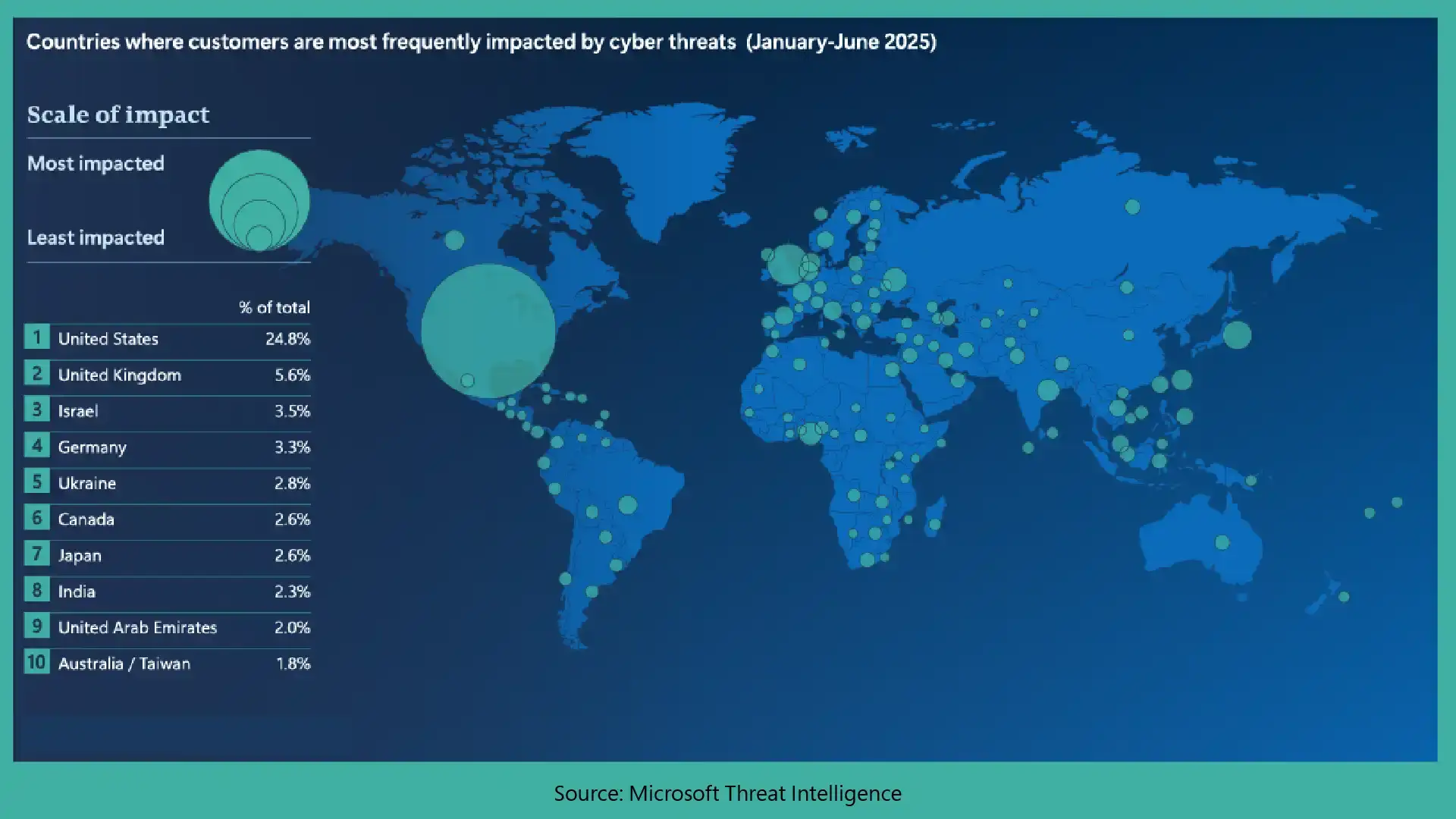
As per the International Journal of Emerging Research in Engineering and Technology research paper, the traditional reactive approaches are not working because cyber-attacks evolve more quickly than defence systems designed to stop them.
Here’s how this evolution is unfolding:
- Wider attack surfaces: The proliferation of IoT devices, at-home working setups, and edge computing nodes increases the virtual real estate attackers can target.
- AI-powered automation: The adversaries today leverage automated scanning bots and AI models to find vulnerabilities before human eyes.
- Behavioral targeting: Adversaries exploit human frailty through AI facsimiles and deepfake social engineering.
- Global impact: Cyberattacks are no longer one-off occurrences — they can disrupt supply chains, economies, and even diplomatic relations.
As per Gartner’s prediction, by 2025, around 45% of the worldwide organizations will have faced attacks on their software supply chains.
This change requires a cybersecurity culture—an active one, if you will—that meld AI-driven detection, rapid response models, and ongoing employee training.
Artificial Intelligence: The New Frontier for Attackers and Defenders
Did you know that around 97% of organizations reported an AI-related breach and lacked proper AI access controls (Cost of Data Breach IBM 2025)?
But according to McKinsey 2025, AI is integrated in cybersecurity tools such as security posture management, Zero Trust capabilities, SASE, and Identity will support users to be more comfortable with the shift in technology and dealing with cyber-attacks in the present and the future.
AI has become the sword and shield in the new cyber war.
Adversaries Fully Embrace AI
- Attack automation: Today, hackers use generative AI tools to automate reconnaissance, phishing, and malware development.
- Agentic AI in Cybersecurity: Attackers are employing agents, AIs capable of performing multistep actions automatically—breaking in, exfiltrating, and covering their tracks without human intervention.
- AI-Driven Social Engineering: Deepfake voice replication and text emulation are being used in vishing attacks that simulate company executives or IT personnel to pilfer credentials.
Did you know that almost USD 1.9M in cost savings are from the extensive use of AI in security? (IBM’s Cost of Data Breach Report 2025)
And as per the World Economic Forum's recent study, they found that around 66% of organizations see AI as the biggest cybersecurity game-changer this year, but only 37% have safeguards to evaluate AI tools before leveraging them.
Prompt Injection: A New AI-Specific Threat
- Prompt injection attacks are being weaponized by cybervillains who trick AIs into skipping safety measures.
- This risk increases as more companies adopt large language models within their internal systems.
- Defenders today block such manipulation using model hardening and content sanitization filters.
Ransomware and Data Extortion: Most Disruptive Threat
Ransomware attacks and data breaches are still the most disruptive threats. Nearly 86% share of businesses experienced a disruption due to a data breach (IBM’s Cost of Data Breach 2025).
What’s Changing in 2026:
- Layered extortion: Criminals aren’t just encrypting victims’ files — they’re stealing sensitive information and threatening to expose it.
- Exploit on the day: Attackers are purchasing and exploiting unpatched vulnerabilities before partners can deploy patches.
- AI-Powered Voice Vishing: Attackers employ synthetic voice imitations to attack staff and sidestep MFA.
These attacks frequently result in cascading economic harm to suppliers, customers, and critical industries such as energy and retail. The only long-term defense is multi-layer resilience: regular offline backups made, employees educated up and down the company hierarchy, threats monitored 24 / 7.
On-Chain Cybercrime Economy
As banks and governments are embracing tokenized assets, hackers are taking advantage of blockchain’s decentralization to obscure their illicit activities.
Emerging On-Chain Threats:
- DeFi and Exchange Hacks: Hackers exploit decentralized finance to siphon crypto assets.
- Malware on the Blockchain: Payloads and command control are being deployed on smart contracts, allowing for persistent adversaries with no single point of removal.
- Token Laundering: The stolen Tokens are being split and shuffled among hundreds of wallets to tens of cents in an effort to dodge tracking.
This has prompted the rise of a new cybersecurity specialization—blockchain forensics and investigation. Analysts must now also learn wallet tracing, smart contract auditing, and Web3 security protocols to battle this decentralized threat economy.
Virtualization, IoT, and Industrial Targets Under Fire
Attackers are thinking beyond making a device unusable and instead focusing on attacking the invisible, digital infrastructure that powers the digital business. Google’s forecast cautioned that hypervisors — the key virtualization software — are at increasing risk of being attacked.
- Hypervisor Bombs: You never know if that next exploit will bring you to your knees with hundreds of virtual machines going down in a matter of hours.
- ICS and OT Attacks: Industrial Control Systems are at greater risk from attacks with ransomware that disrupt critical operations.
- Metaverse & AR Portals: ICCK Transactions on Intelligent Systematics (2025) claims that AR/VR ecosystems have inherent security risks – digital ID management, decentralized storage are some areas where the AR/VR relies on, as well as biometric data use.
These ever-expanding environments introduce sophisticated threats and complex attack surfaces that require multi-disciplinary defences involving cloud security, IoT device monitoring, and human factor protection.
Preparing for Threats to Come in the Future
-
Advanced Technologies Evolution for Cyber Defense
According to the ICRCEDA 2025 conference paper, three evolving technologies will shape the future of cyber defense:
- Quantum-resistant Encryption: Classical RSA and ECC encryption might become vulnerable when quantum computers become super powerful and mature. Post-quantum cryptography standards are already being developed to protect data from quantum decryption to protect against highly advanced decryptions.
- Zero Trust Architecture (ZTA): Rather than automatically trust devices or users, ZTA checks all requests — perfect for remote work and hybrid-cloud environments.
- Behavioral biometrics and AI threat prediction: The continued observation of user behavior, together with an AI model for prediction, can detect insider threats before they do any damage, as well as prevent breaches.
These advances turn cybersecurity from a static wall of protection into an active, adaptive system that can react to new threats in real time.
-
Building Resilience: From Cybersecurity Training to Continuous Learning
Tech moves quickly — but people need to move faster. While AI systems manage security, human involvement and critical thought continue to be the bedrock of cyber defense.
- Many top companies are focusing on ongoing cybersecurity education as the best defense against 2026’s complicated threat matrix.
- Online cybersecurity certifications now offer courses in AI defense, blockchain forensics, and quantum-safe encryption.
- Cybersecurity professionals need to upskill every year if they wish to be effective in the field.
- The top cybersecurity certification courses train learners on threat simulations to ready students for actual attacks.
This culture of endless learning will determine who takes the lead in cybersecurity over the next decade — and who falls by the wayside.
Staying Ahead in a World of Evolving Threats
The future attacks won’t be silly, slow, and predictable. However, defenders who adopt AI security, Zero Trust models, and perpetual learning can stay a step ahead of even the most sophisticated attacks.
Cybersecurity in 2026 is not just about tools — it’s about people who are ready to do battle on an AI-powered battlefield. Explore the top cybersecurity trends to get insights about the future of cybersecurity and threat advancements. If you are ready to upskill and prepare yourself to protect against the emerging advanced cyber-attacks in 2026 and beyond. It’s your time to shine as a cybersecurity specialist!





