

Top 8 Cybersecurity Trends to Watch Out in 2026
Cybersecurity has become a strategic necessity for businesses, governments, and individuals in today’s hyper-connected world. As digital transformation accelerates, organizations face increasingly sophisticated threats, from ransomware and phishing to AI-powered attacks, that exploit vulnerabilities across industries. Staying resilient requires advanced technology, skilled professionals, and adaptive strategies to protect critical data and operations.
IBM’s Cost of a Data Breach Report 2025 shows the global average breach cost at $4.4 million, with 97% of organizations experiencing AI-related incidents lacking proper access controls. Organizations using AI in security reported $1.9 million in cost savings, highlighting the growing importance of AI-driven defenses. In this blog, we explore key cybersecurity trends, their applications, and why they matter, along with other key emerging threats shaping 2026.
1. Agentic AI Attacks and Autonomous Defenses
Artificial Intelligence is transforming cybersecurity for attackers and defenders alike. AI agents can independently scan networks, develop adaptive phishing campaigns, and execute sophisticated attacks. On the defensive side, AI-enabled systems can identify anomalies, quarantine threats, and patch, in real time, vulnerabilities with limited or no human intervention.
Key Use Cases:
- AI-driven phishing campaigns that adapt to human behavior
- Autonomous Security Operations Centers (SOCs) that respond instantly to threats
- Predictive AI models that anticipate attacks and recommend countermeasures
What to Expect by 2026:
- AI-driven systems will monitor and respond to threats instantly, increasing limits on time-consuming processes.
- Predictive AI models will provide advanced organizations with coverage before they can be attacked and raise their overall security posture.
- Autonomous SOCs will allow security teams will focus on strategic initiatives while threat patterns are handled automatically.
- Organizations will strengthen their ability to sustain operations and protect their critical data against new and novel threats.
“According to the RSA Conference, agentic AI introduces new attack vectors like prompt injection and model hijacking, making AI-driven monitoring and layered defenses critical.”
Why It Matters:
In a landscape where adversary attacks are automated, organizations that utilize AI-enhanced cybersecurity gain a unique advantage. Using AI mitigates the risk of human error and allows organizations to even stop threats before they develop. Professionals with AI cybersecurity skills will be in demand.
2. Deepfake and Synthetic Cyber Attacks
The emergence of synthetic content, text, audio, video, and even 3D assets created by AI is a major development in cybersecurity. Deepfakes and AI-based media as a whole are not merely a new phenomenon; rather, it is serving to amend the way in which today's attackers operate, as well as how organizations respond, giving rise to innovations in defenses and detection.
Key Use Cases:
- AI generated video calls and audio messages for highly customized phishing and vishing campaigns
- Automatic email scams from synthetic data that are more convincing in social engineering
- Complex disinformation campaigns using realistic AI-generated content to influence decisions and perceptions.
A Look Ahead:
- Significantly more sophisticated deepfake attacks specifically targeting individuals and organizations will arise
- AI-embedded detection tools as part of the platforms to identify synthetic content in real time
- Organizations will incorporate synthetic content monitoring as part of standard practices for managing cyber risk
Why It Matters:
Synthetic cyber threats are shaping the future of digital interactions. Organizations need to adopt advanced strategies for detection, monitoring, and verification using AI. Cyberspace professionals familiar with the usage of synthetic technologies will have a critical role in managing this evolving phenomenon.
3. Ransomware-as-a-Service (RaaS) Expansion
As ransomware continues to develop, even non-technical criminals may now launch attacks thanks to ransomware-as-a-service. RaaS systems reduce the entry barrier for cybercriminals by offering malware, tools, and detailed instructions.
Important Use Cases:
- Automated ransomware attacks directed against essential infrastructure and businesses
- Malware boosted by AI that changes to evade security measures.
- Multi-phase attacks include ransom demands, data exfiltration, and encryption
By 2026, expect to see widespread use of RaaS and more complex attack tactics, AI-driven ransomware that can instantly detect vulnerabilities, and increased focus on vital industries like finance, healthcare, and energy.
Why It Matters:
Ransomware attacks pose severe risks to operational continuity and financial stability. Organizations must combine automated defenses, secure backup strategies, and employee awareness to mitigate risks. Cybersecurity professionals skilled in ransomware defense will be highly sought after. As highlighted in our blog “How to Remove and Recover from a Ransomware Attack,” rapid detection, isolation, and recovery plans, along with AI-powered monitoring and staff training, significantly improve resilience.
4. Strengthening the Human Factor
Despite advances in technology, humans are still the weakest link in the cybersecurity chain. Phishing, social engineering, and insider threats find their advantage in human behavior; one human error could put a whole system at risk.
Key use cases:
- Continuous cybersecurity awareness training for employees
- Simulated phishing campaigns to test employee awareness and responsiveness
- Insider threat monitoring using behavioral analytics
What to expect by 2026:
- Gamified, continuous training programs that are part of a company's culture
- Employee engagement is a part of their cybersecurity culture
- Reduction in the number of breaches due to human error
Why it matters:
Human-centric strategies are critical to sort out attacks that technology will never stop. The professional with both technical skill and knowledge of social engineering will be more effective in protecting the organization; thus, knowledge of human factors in the domain will be a vital cybersecurity skill.
5. Quantum-Safe Security
Quantum computing poses a risk to traditional encryption that supports modern cybersecurity. Organizations are already adopting post-quantum cryptography to ensure their data is safe against attacks via quantum technologies in the future.
Key Use Cases:
- Quantum-resistant encryption for cloud-based communications
- Safeguarding government and financial data against possible quantum breaches
- Augmenting existing IT infrastructure with post-quantum security solutions
What to Expect by 2026:
- Mass adoption of quantum-safe encryption in enterprise applications
- Initial adoption in sensitive areas like banking and healthcare
- Everyone will take a proactive approach to consider long-term security issues related to quantum computing.
Why It Matters:
Quantum computing will eventually render current encryption obsolete. The earlier an organization prepares, the better it will protect sensitive information and trust. Knowledge of quantum security will result in job security for cybersecurity professionals.
6. Regulatory and Legislative Overhaul
Countries around the world are strengthening cybersecurity regulations, increasing the mandatory requirements for organizations to protect data and report incidents. The following use cases outlined below are designed to give you a sense of the direction that is developing around cybersecurity regulations:
Use Cases:
- Mandated risk assessments and audits to be conducted across all industries
- Compliance with the EU NIS2 Directive and Digital Operational Resilience Act (DORA).
- Penalties for breaches or non-compliance with regulations.
What to Expect in 2026:
- Regulatory compliance is a need rather than simply a desire for the business's continuity.
- More transparency and reporting expectations.
- Integration of cybersecurity programs into governance, risk, and compliance (GRC) programs.
Why it Matters:
Non-compliance can lead to adverse fines, loss of business, and reputational damage. Organizations that are committed to compliance strategies will gain recognition, compliance, and reduced first- and third-party risk.
7. Cyberwarfare and Geopolitical Threats
State-sponsored cyberattacks are becoming an increasingly important trend in cybersecurity, aimed at national infrastructures, strategic industries, and sensitive data. These attacks are not just technical but also express geopolitical tensions and emerging aspects of cyberwarfare, contributing to global strategy.
Key use cases include:
- Disruption of national energy grids, hospitals, and financial systems;
- Theft of sensitive data for political, economic, or military advantage;
- Public and private partnerships for enhancing cyber defenses;
What to expect by 2026:
- It is likely to be more recognized as an essential aspect of national security.
- There will likely be increased public-private partnerships aimed at preventing large-scale attacks.
- Organizations will be developing resilience strategies to continue operations during a cyber conflict.
Why it matters:
Cyberwarfare has unique risks that arise beyond IT systems, including implications for societal stability, national economic security, and organizational continuity. Understanding this trend can help organizations mitigate risks more proactively, create more effective strategies for resilience, and navigate through geopolitical cyber threats.
8. Neuromorphic Mimicry Attacks: Exploiting Brain-Inspired Computing
Neuromorphic computing, which draws inspiration from the neural organization of the human brain, is advancing the fields of artificial intelligence and edge computing with its low-power, adaptive, and event-driven architecture. Unfortunately, these characteristics also create new cybersecurity vulnerabilities.
Key Use Cases:
- Autonomous Vehicles: Real-time processing for self-driving automobiles is made possible by neuromorphic processors. They may, however, be vulnerable to attacks that imitate real cerebral activity, which could result in accidents or malfunctioning vehicles.
- Smart Medical Implants: Neuromorphic computing is used in devices such as neurostimulators and pacemakers to provide adaptive responses.
- Internet of Things (IoT) Networks: IoT devices are increasingly using neuromorphic processors for computing power. By taking advantage of these technologies, attackers may interfere with industrial sensors, smart household appliances, or environmental monitoring equipment.
What to Expect by 2026:
- Growing Adoption: The integration of neuromorphic computing into key systems will expand as neuromorphic computing becomes more prevalent.
- The Rise of Neuromorphic Mimicry Attacks (NMAs): NMAs will take advantage of properties of neuromorphic chips, such as probabilistic and non-deterministic, to conduct stealthy intrusions that evade detection from standard intrusion detection systems.
- Creation of Mitigations: Research will be directed toward forming neural-specific anomaly detection systems and secure synaptic learning protocols to counter NMAs.
Why It Matters:
Neuromorphic computing has the potential to fundamentally enhance the efficiency and flexibility of processing systems. Nevertheless, its unique features also introduce new risk factors. Therefore, understanding and mitigating risks is essential to protecting the security of systems with neuromorphic chips.
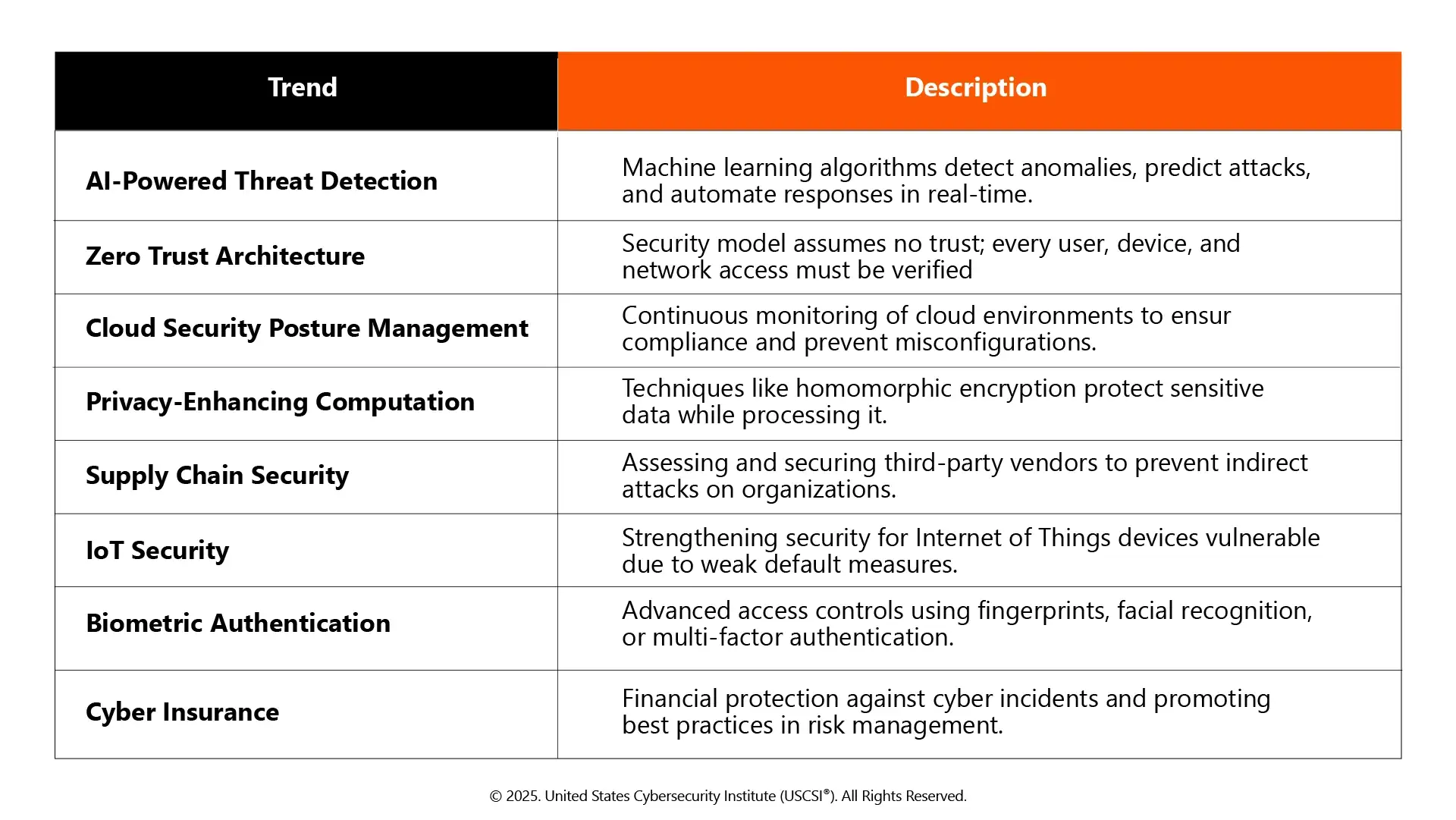
Additional Emerging Cybersecurity Trends in 2026
Conclusion
The cybersecurity landscape of 2026 will be shaped by AI-centric threats, quantum threats, and changing global regulations. Organizations that focus on state-of-the-art adaptive defenses and talent will continue to thrive in a complex operating environment.
For the individual, this translates to upskilling in AI-based security, ransomware defense, and quantum-safe processes. The United States Cybersecurity Institute (USCSI®) offers vendor-neutral cybersecurity training programs geared towards developing these capabilities for the future.
In a world of threats that change daily, you must pair the right knowledge with the appropriate career path in cybersecurity.





