

How to Remove and Recover from a Ransomware Attack?
Ransomware is one of the most disruptive security threats. It's a malicious software that infects files, systems, or an entire network, preventing access to them until a ransom/attacker is paid.
Ransomware is still the fastest-growing form of cybercrime. Far from slowing down, it’s projected to cost nearly $275 billion annually by 2031, according to Cybersecurity Ventures. With attackers launching a new strike every two seconds and continually refining their malware and extortion tactics, the threat is only escalating.
Ransomware in organizations can mean operations grind to a halt, it can lead to serious financial consequences, and it can adversely affect the reputation. Being able to eliminate ransomware and recover from it is an important skill for any business or person nowadays.
Recent Updates on Ransomware Cyberattacks:
Here are some key statistics related to ransomware cyberattacks in the recent past (as of Q2 2025):
Allianz Life Breach (July 2025): The personal data of roughly 1.4 million U.S. customers — names, addresses, phone numbers, and email addresses — were accessed, leading Allianz to provide two years of identity monitoring. (Security Affairs)
Key findings by IBM and Ponemon Institute analysis:
- $4.44 million Average global cost of a data breach in 2025, a decrease of 9% compared to 2024; U.S. breaches surged to a record $10.22 million.
- 97% – Businesses that suffered cyber-attacks involving AI had not had sufficient AI access controls, highlighting how AI presents an increasing security risk.
- $1.9 Million – Monetary savings achieved by firms applying AI and automation across their security operations.
Most Common Ransomware Attack Vectors
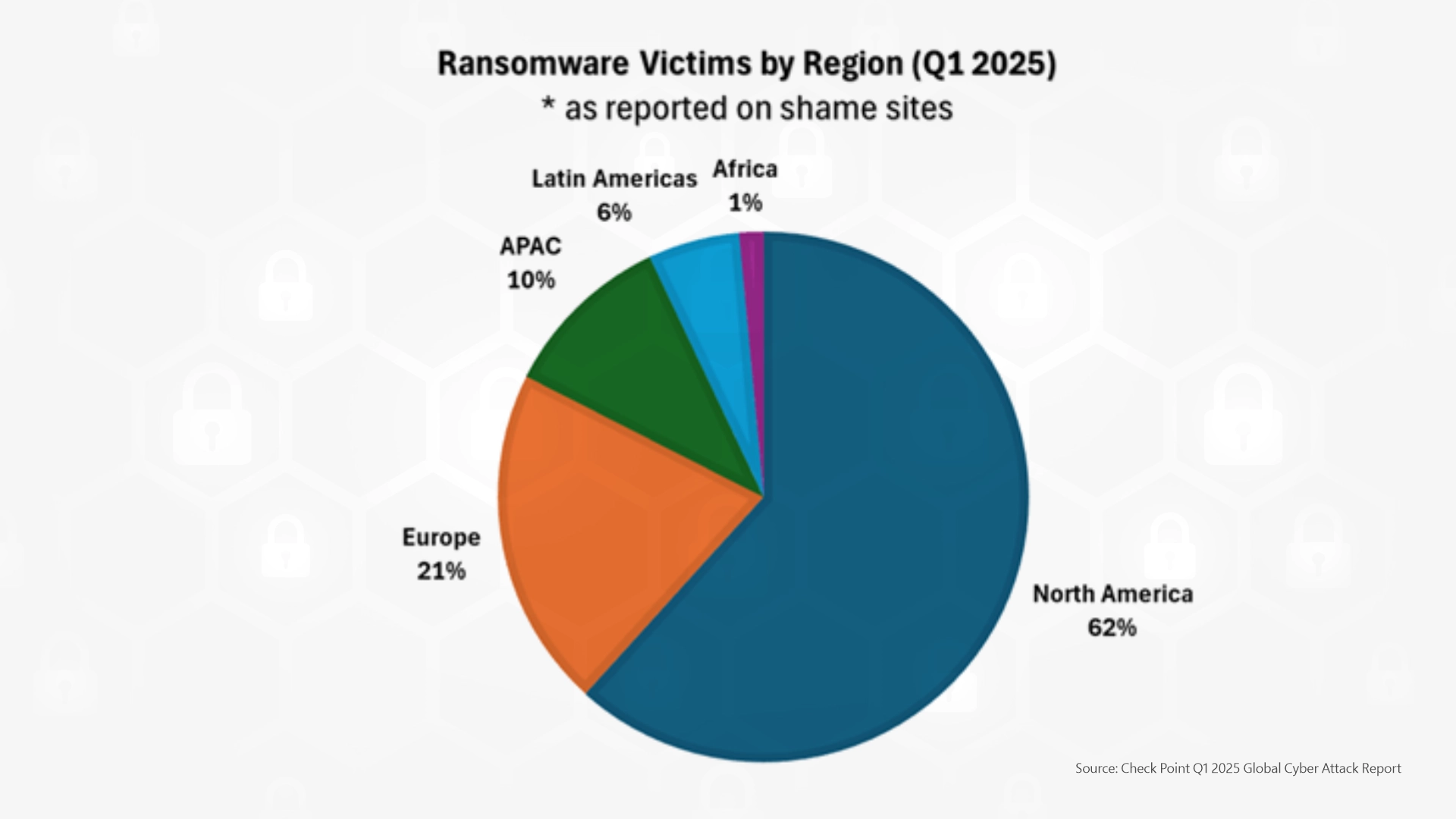
Ransomware incidents surged by 126% from Q1 2024, reaching 2,289 reported cases by Q1 2025. North America was the most heavily affected region, accounting for 62% of attacks, followed by Europe at 21% (Source: Checkpoint Research).
Can Ransomware be Removed?
Consider the following scenarios:
- If the ransomware is blocked from encrypting sensitive data, the answer is yes.
- If it slips past defensive solutions and locks important data using strong algorithms, then no.
- Whether or not decryption tools are available for that strain of ransomware, it’s a maybe.
Perfect timing is essential — early detection, rapid isolation, and detection with security tools help increase the odds of successful removal. But with sophisticated encryption, deciphering the code itself soon becomes the hardest part.
Now, let’s explore detailed instructions on how to get rid of ransomware step by step and how to recover from a ransomware attack with a comprehensive response plan.
How Can You Remove Ransomware?
- Detect and Analyze
The first thing is detecting abnormal incidents like huge numbers of files being encrypted or any unauthorized access attempt. Files or processes that are suspicious should be isolated and checked properly. Apart from this, a careful awareness of even a small malicious attempt can help you detect ransomware easily. All you need to do is be attentive and alert about such events
- Continuous Monitoring & AI Analytics: Employ EDR/XDR solutions, firewalls, IDS/IPS, and AI/ML threat detection to constantly monitor networks in real time and identify and raise alerts of unusual activity or irregularities.
- Log & File Integrity Verifications: Review access control logs and file alterations for unauthorized access or alterations that would indicate ransomware activity.
- Employee Awareness & Alerts: Increase awareness among employees to identify phishing and set up real-time alerts through dashboards or text and calls to take action as fast as you can.
- Block the Corrupted Files
Stop the spread of ransomware the moment it is identified. You can use anti-ransomware software to quarantine files and systems infected by ransomware and prevent further access to the rest of the network. It will help you contain the threat locally and make it easy to manage and clean up.
- Decrypt Locked Files
When files are encrypted, the attention moves to decryption. There are ransomware programs that come with a decryption feature as part of their tools. In some situations, organizations can also turn to outside decryption tools available from security vendors, or they could partner with a cybersecurity professional. If decryption is unsuccessful, potential recovery options include using the most recent backups.
- Real-Time Protection
A lot of EDR (Endpoint Detection and Response) solutions have something similar to real-time monitoring. They stop malicious downloads, links, or suspicious activity before there is any chance the malware can enter. The maintenance of these protective measures helps in removing ransomware.
- System and File Recovery
Once decrypted or restored from backup, a full system and file scan should ensure that all is clear and there is no malicious program or software present. Tools for recovery make the data safe to use and contain no hidden, harmful code.
- Notification and Reporting
All ransomware incidents need to be logged and communicated. Dashboards and alerts delivered automatically offer visibility into how the threat was discovered and mitigated. Such feedback is useful for further designing and improvement.
- Post-Event Support
Now all that is left to do is the forensic work. By understanding how ransomware got in and moved across the network, organizations will be better positioned to heighten their defences. Some experience has been gained here, which can prevent a recurrence.
Ransomware Recovery Options Explained
Although removal mitigates an immediate risk, recovery enables an organization to overcome the effects of ransomware. A robust response recovery plan to ransomware enables this to happen.
- Backups First
If you have good backups, recovery is your only real option. Data, code, and systems need to be backed up regularly, tested on a consistent basis, and stored offline or in safe cloud systems. If you have no safe backups, then it will be difficult to recover from ransomware that much harder to recover.
- Incident Response Plan
A written ransomware response plan sets forth tasks to be performed during an attack. It defines decision points, communication roles, and levels of authority. This should update action plans that are exercised with simulations and attentiveness.
- Train and Practice
Businesses need to invest in cybersecurity training programs to teach staff to take action promptly. Exercises and war games enable teams to rehearse managing real-world attack situations.
- Isolate and Contain
Whenever ransomware is detected, the security team needs to plan and isolate all individual systems. These practices help in preventing the spread of ransomware, which may also involve cutting off command-and-control communications and following zero-trust network guidelines.
- Communicate Clearly
Recovery also depends on communication. Stakeholders, employees, and sometimes customers require timely updates if such attacks happen.
- Restore Systems Safely
Once recovered, the organizations could then start wiping and rebuilding their endpoints. Data from backups must be checked for infection before being restored. Bringing back up core apps and storage systems is necessary to get operations running again.
- Review and Improve
Conduct an after-action review once you have recovered. Find what worked, what didn’t, and how to improve. This reinforces defences and better prepares teams for a safe and secure future.
Why Preparedness Matters for Ransomware?
Ransomware recovery is never instantaneous. It may take days or even weeks to restore some types of data, and it costs many organizations. In addition to the direct costs of cybersecurity tools and staff time, there are productivity losses and potential penalties for organizations.
A robust cybersecurity approach, with the help of cybersecurity training programs for team upskilling, and the use of investments in anti-ransomware tools, could potentially mitigate this risk. For professionals, pursuing a career in cybersecurity with continued education and robust cybersecurity training helps them tackle these changing threats.
Wrap Up
Ransomware is now a significant threat to businesses and individuals. But the protection from it can’t just be about acting after an attack; protecting from it requires a definitive plan of swift action. Stopping ransomware before it has the chance to spread can be a time saver, can help prevent data and monetary loss.
Ransomware attacks are becoming more sophisticated, requiring quicker detection, better defences, and expert cybersecurity teams. Future readiness will depend on AI-powered security, frequent backups, and ongoing employee education to mitigate the damage.
Do use decryption tools and keep regular backups so you can recover files safely. A sound ransomware response plan, consistent cybersecurity training programs, and good communication with employees and stakeholders are all necessary to ensure the business continues running with minimal disruption. After an attack, understanding how it happened and evaluating how you responded can prevent it from happening again.





