

Can Digital Twins Transform the Future of Cybersecurity?

Industry giants such as Trellix have been deploying approaches that leverage data from sources such as Microsoft Active Directory and network policies to build a detailed digital replica of a customer’s enterprise environment. AI agents thereafter operate within this model to triage alerts, reconstruct potential user activities, and assess the possible effects of suspicious behavior. That is enough reason to understand what the big deal is about Digital Twin in Cybersecurity.
This significant evolution of the digital twins, as being envisioned and deployed as cybersecurity strategists is a massive leap in the entire domain. With generative AI becoming extremely proficient at understanding systems and environments; retaining the benefits of utilizing them for the longest term is a work of art and sheer skill. This calls for an urgent upskilling in cybersecurity training programs. By the way, do you know the latest upgrades in the cybersecurity industry that you might have missed on; keep reading!

Highlighting the concern or more-so a trend for the vast cybersecurity future at the Gartner Security and Risk Management Summit, Sydney; recently- building a sustainable fast-laned security evolutions is a must.
From the advent of firewalls and antivirus software in late 1990s, to cryptography and cloud computing to multi-factor authentication; the world of cybersecurity has evolved multiple folds. Understanding this transition is key to neutralizing the impact of malicious threats that have been evolving at a staggering rate as well. Fighting the emerging and ever-nuanced security threats is inevitable to safeguarding the critical information and network systems. Chris Novak, Leading Security Expert, Author, and Member of the Forbes Technology Council, champions data sharing and research-driven analysis of cybersecurity incidents and data breaches to help the entire industry become safer. He stresses on the fact that cybersecurity is gaining significant momentum in 2025; yet there are still many challenges to address, holding the entire security ecosystem together remains a concern. This leads us to unraveling the critical role the latest addition ‘Digital Twins’ have to make in line. Let us explore together.
Knowing Digital Twins:
Virtual Replicas of physical objects, systems, and processes, aka, Digital Twins, have been garnering attention in the global tech space worldwide; specifically in the network and security departments. Understanding these Gen AI-powered virtual environments, and how they are boosting operational security is definitely a game-changer for the future of cybersecurity across industries and global sectors of work.

Digital Twins- Dimensions Explored
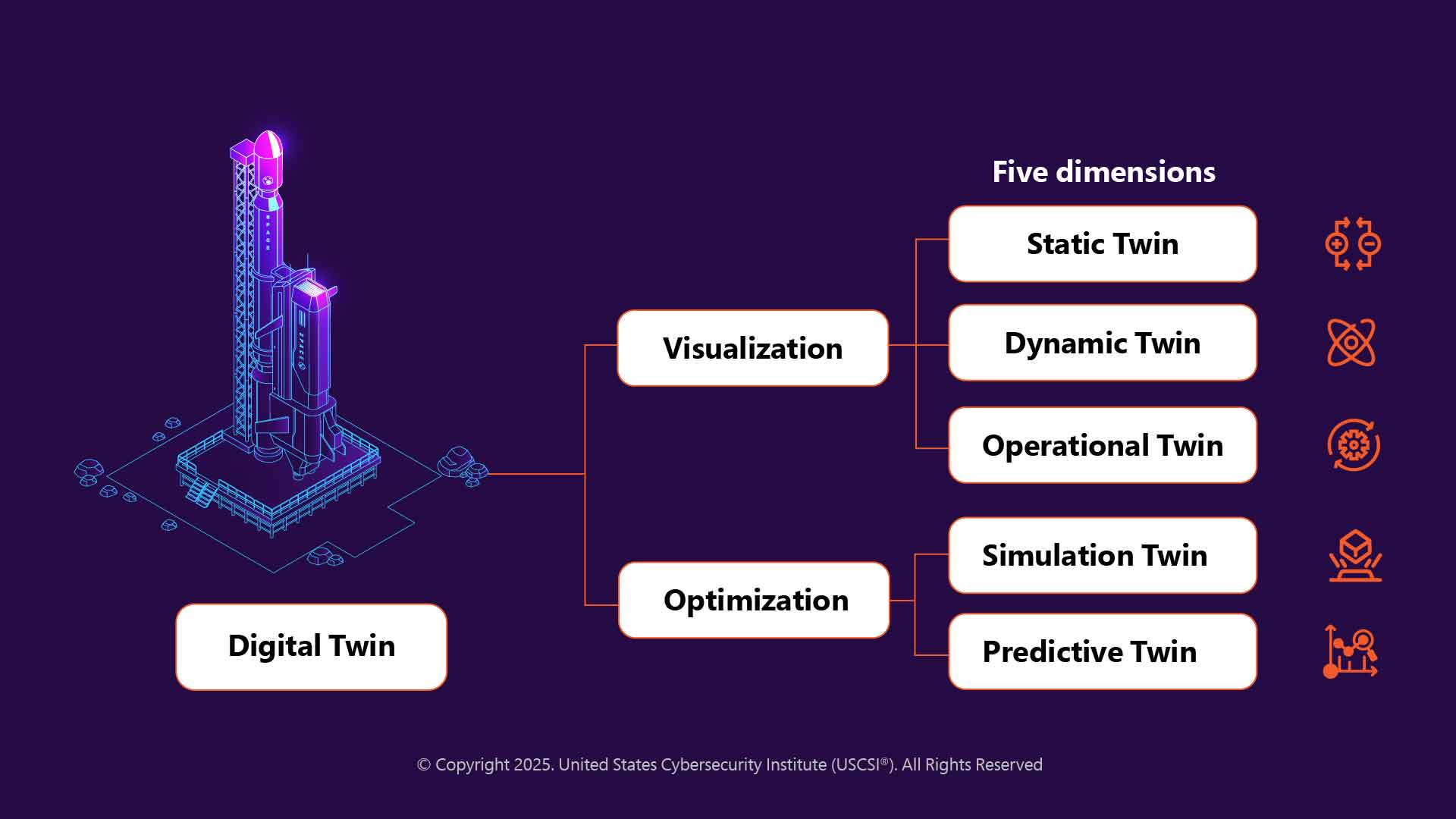
-
Visualization- Incorporates taking a physical object or abstract process and digitizing it. It takes form in three dimensions including- Static (rudimentary twin), Dynamic (representation of its physical twin at the same point in time), and Operational (the digital twin truly comes alive in this).
-
Optimization- Incorporates automatically optimizing their real-life counterparts as they go beyond data and predict what might happen in the future. It includes Real-time simulation twins, and Predictive twins.
Digital Twins for Cybersecurity- Good News or Otherwise?
Many debates about the impact of digital twin technology on businesses and industries of diverse shapes, sizes, and performance. Looking at the recent advances, one thing is clear that the industries are benefiting big time with the Cyber Digital Twins (CDTs) becoming an active part of their environment. These evolutionary tools incorporate GenAI, empowering teams without specific network or security expertise to query the models. Let us take a closer look at its positives and negatives, as elaborated below.
Powerful Ramp-ups- Benefits:
With digital twins in action, industries are making big moves as regards enhanced scenario planning and testing. Digital twins emulate live production environments, allowing organizations to test changes in a controlled manner.
- Minimising Disruption and Downtime
- Leveraging AI to Simplify Interactions
- Enhanced Operational Resilience
- Improved Product Delivery and Developer Efficiency
- Predictive Maintenance and Anomaly Detection
- Simulate Cyberattack Scenarios in a Controlled Environment
- Enhanced Visibility through Augmented Reality and AI Integration
Apart from these benefits listed above, digital twins act as a pivot by offering core capabilities such as:
- Physical Security- Designing an effective security system for a physical environment requires careful consideration of many variables. Inadequate or poor placement or overloading the system with cameras and high-tech gadgets can lead to unnecessary expenses and uninvited vulnerabilities. You can experience a 10-50% cost savings in physical security projects by optimizing security setups and configurations (WEF).
- Network Twins- It cuts through the challenges by providing a comprehensive, real-time replica of the network, enabling seamless validation and verification of configurations and security policies. These Network digital twins are a transformational technology that can cut request delivery times by up to 20% (Gartner).
- SOC Twinning in IT and OT Worlds- With the designing virtual replicas of organization’s IT and operational technology infrastructure; security teams can simulate potential cyberthreats in a controlled environment. AI has reduced breach detection times by 33% and containment time by 43% in security operations centre (SOC) (see Figure 1).
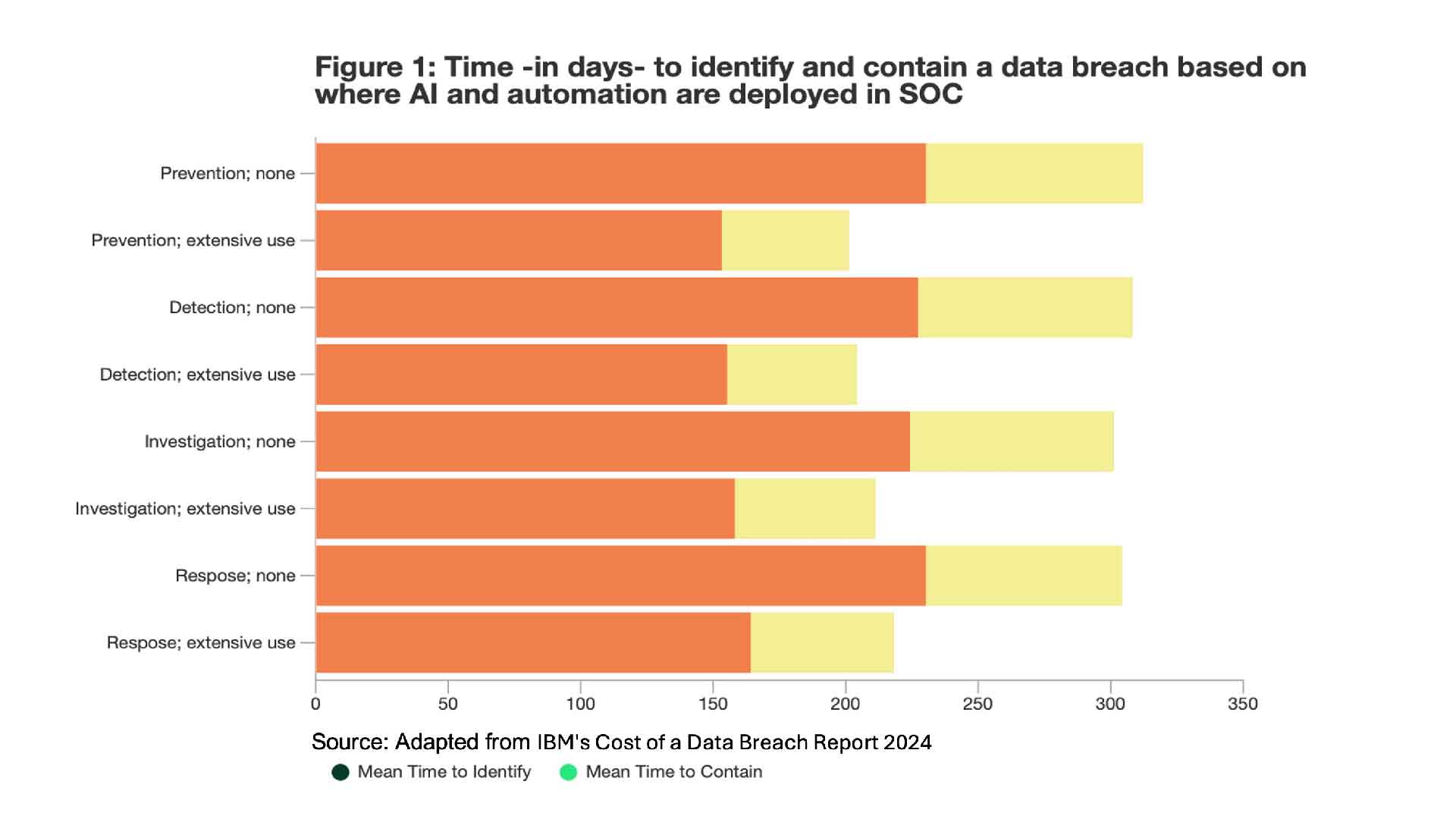
With digital twins taking over the scene worldwide, and AI Agents becoming a core companion at workplace- understanding the ins and out of this mean tech tool is a must for organization-wide cybersecurity.

Challenges and Ethical Hiccups:
- Security of Digital Twins
Use of encryption, robust authentication, and continuous monitoring of digital twins data streams are essential to mitigate these risks.
- Data Integrity and Privacy Concerns
Ensuring that data is accurate and updated is a vital requisite to maintain the effectiveness of cybersecurity defenses.
- Cost and Complexity of the Digital Twin System
Lack of resources for continuous monitoring and real-time synchronization of physical and digital systems is a must. This also adds up the critical role of empowering the cybersecurity workforce with the reuisite skills and cybersecurity certifications to fight the battle with the top security armor.
- Data Collection
Organizations must establish policies and frameworks to ensure ethical data collection, processing, and sharing. The ethical use of digital twins in cybersecurity should account for transparency and accountability in decision-making; thereby leveraging technology for the best results possible.
- Compliance with Data Protection Regulations
Adhering to the security norms laid by the eminent GDPR and HIPAA is critical as implementing practices such as data anonymization and secure data handling helps meet regulatory requisites and protect sensitive information, and build lasting trust.
Emerging Technologies and Future Directions:
Digital Twins are set to transform the way organizations operate by revolutionizing network management and cybersecurity via dynamic, real-time, and comprehensive approach to managing, optimizing, and securing complex systems. Let us explore the future map for digital twins technology right here:
For long, nothing substance has been said about empowering the future security workforce with the right amount of relevant futuristic cybersecurity skills, tools, and technologies to fight the unknown. Gaining skill strength with the most trusted cybersecurity training programs; that are a balanced mix of recent industry evolutions and make you an expert in dealing the rising menace like a pro. Resonating with your long-term professional goals is a must as cybersecurity is not going anywhere, and so does the demand for seasoned cybersecurity specialists. This is your responsibility to close the widening security skills talent gap worldwide; by gaining the right nuances today. Solidify your cybersecurity career with the best credentialing partners today!





