

How to Secure RAG Applications? A Detailed Overview
Retrieval-Augmented Generation (RAG) is one of the most fascinating architectures in the field of AI. It uses Large Language Models (LLMs) with external knowledge sources like databases, vector stores, and document repositories to provide more accurate and contextual responses. Therefore, RAG is widely used in critical industries like finance, healthcare, law, and customer services.
However, its biggest strength also poses a new attack surface, i.e., reliance on external retrieval. RAGs are more prone to risks like prompt injection, data poisoning, or information leakage as compared to static LLMs. Therefore, organizations must consider RAG application security as a layered challenge, including data, infrastructure, models, and governance, for maximum safety.
Top Security Risks in RAG Applications
The following are some of the key risks to RAG application security that organizations need to be aware of:
-
Prompt Injection Attacks
Cyberattacks create malicious inputs to change the model’s behavior. For example, they can embed hidden instructions in retrieved documents to trick the LLM into leaking data
-
Indirect Injection through Retrieval Sources
Even more sophisticated, attackers can inject hidden adversarial instructions in public data, such as websites or open documents, that can lead to bypassing traditional input filters
-
Data Leakage and Privacy Risks
RAG mostly pulls data from proprietary or sensitive datasets. So, if there are no strict controls, then there are chances of exposing confidential or personally identifiable information (PII)
-
Supply Chain Risks
Sometimes, the open-source models, embeddings, and external APIs that feed RAG may also include compromised components.
-
Hallucination
Even with retrieval, the Large Language Models may generate incorrect outputs or blend irrelevant documents that can lead to incorrect facts or serious security consequences.
-
Denial of Service (DoS) Risks
Attackers can also overload the retrieval pipelines and flood the models with expensive queries that would degrade their performance and make applications unavailable.
Securing RAG Applications at Each Stage
Now, the important part - how can cybersecurity experts, in collaboration with professionals from other domains, secure RAG applications? Well, to defend these AI agents against various risks that we discussed above, organizations need to adopt a defense-in-depth approach at every stage, as follows:
-
Data Ingestion
This stage involves collecting, validating, and storing data from external sources. Since it directly influences the model that is retrieved later, it is essential to ensure security at this stage. It can be done by:
- Use only trusted data sources and audit external APIs regularly
- Sanitize inputs to block malicious scripts and poisoned data
- Enforce schema validation to reject invalid inputs
- Employ data encryption with HTTPS/TLS
Pseudocode for secure ingestion
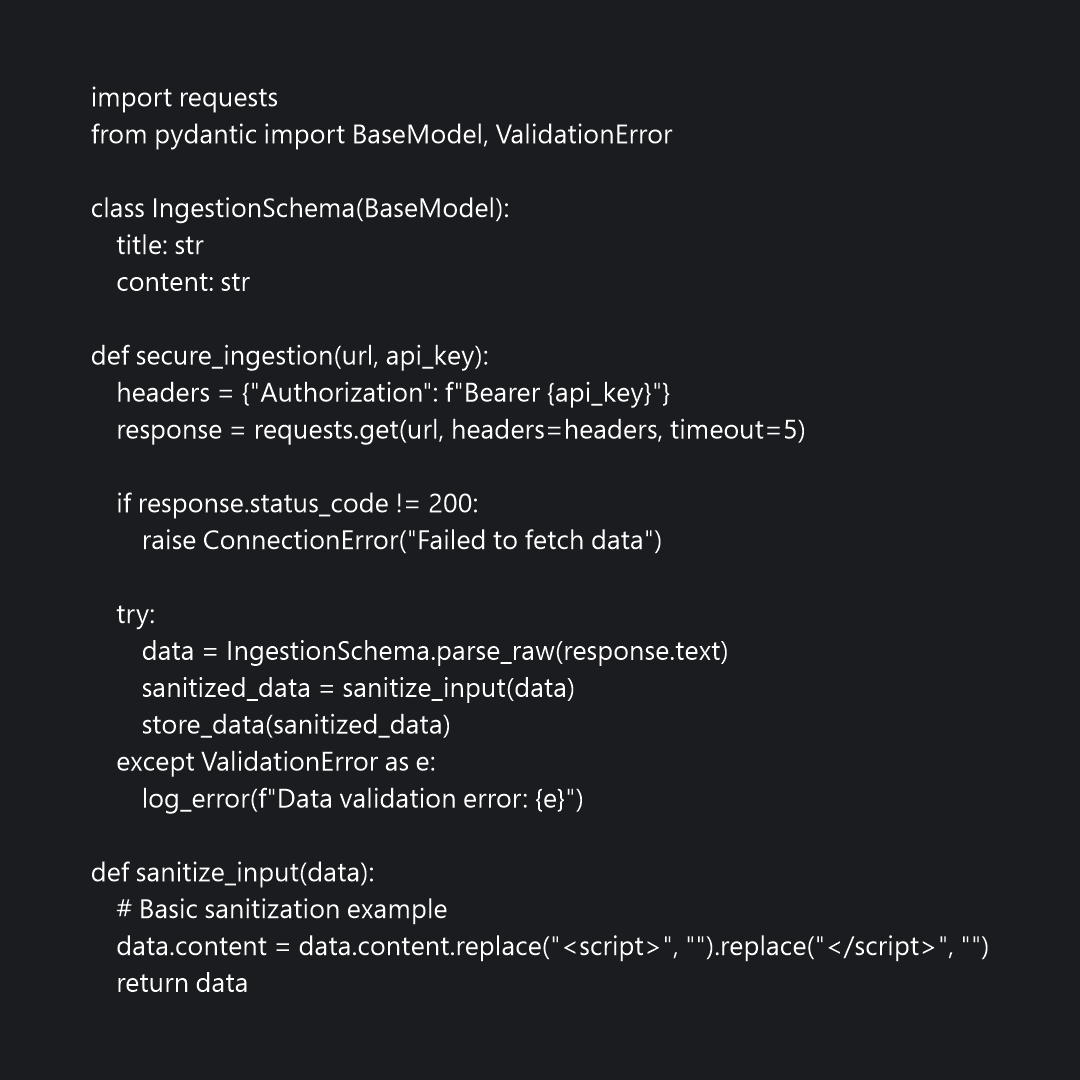
-
Data Storage
Securing this stage is also important to prevent tampering and ensure data integrity. The following are the best practices to secure RAG applications at this stage:
- Store data in WORM (write-once, read-many) formats to prevent tampering
- Use version control to roll back changes in case of poisoning
- Enforce Role-Based Access Control (RBAC)
- Use AES-256 or equivalent standards for data encryption at rest
-
Pre-Processing
In this stage, data needs to be cleaned and standardized to be embedded into vector spaces for retrieval. Any compromise in this stage can be exaggerated in the RAG pipeline. Securing this stage involves:
- Standardizing data cleaning, normalization, and indexing workflows
- Restricting pre-processing scripts with least-privilege access
- Detecting anomalies using statistical methods to identify unusual patterns
- Monitoring deviations in data distribution to detect suspicious activities
Pseudocode for anomaly detection
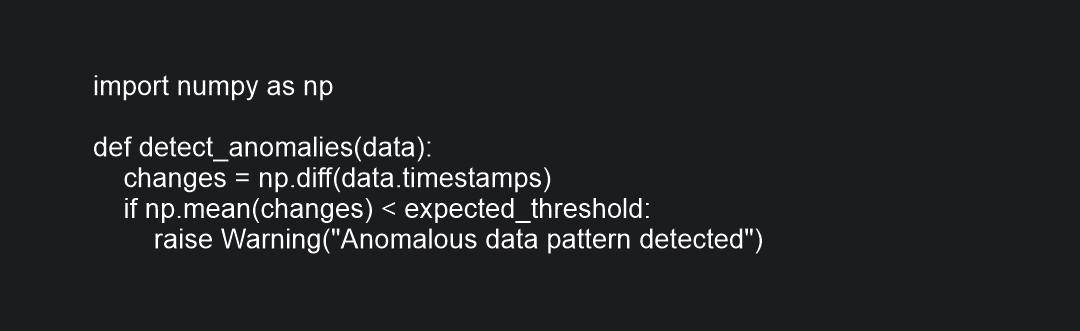
-
Retrieval and Querying
AI agents fetch documents or embeddings from the knowledge base in response to user queries in this stage. Failing to secure at this stage can lead to attackers exploiting it through malicious queries or adversarial embeddings.
Best practices:
- Use parameterized queries to block injection attacks
- Embeddings should be regularly validated for integrity and consistency
- Set limits on the number of queries that each user can make to prevent abuse
-
Generation
This phase refers to retrieving data being passed to the LLM for augmentation. It is essential to secure it for better accuracy, safety, and trust. To secure this stage, cybersecurity professionals can:
- Provide citations or links to the retrieved document sources
- Allow users to view retrieved data alongside generated responses, and
- Use heuristics or AI-based tools to validate response quality
Pseudocode for response validation
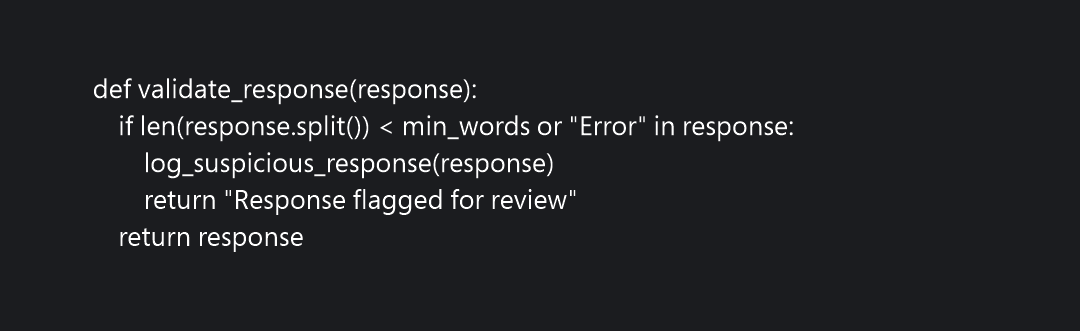
Other essential methods to secure RAG applications:
Apart from the steps we discussed above for RAG applications security at each stage, there are other things that should be taken care of, like:
- Verifying the integrity of the model through checksums and restricting dependencies to trusted sources only
- Implementing privacy by design by anonymizing sensitive data and adopting region-specific controls for compliance with different nations
- Secure architectures should be resilient to DoS attacks through caching, rate-limiting, or fallback mechanisms
Apart from these, Large Language Models can be a very efficient tool in eliminating several cybersecurity risks and secure our future. Learn how LLMs enhance cybersecurity and protect from various threats.
A Secure RAG Architecture
A layered security pipeline can look like this:
- User Layer: Authentication, authorization, and identity verification.
- Input Layer: Sanitization filters to block malicious encodings and injections.
- Prompt Layer: Structured templates with guardrails and salted tags.
- Retrieval Layer: Secure vector stores with RBAC, encrypted data, and vetted documents.
- Model Layer: LLM generation with resource constraints and monitoring.
- Output Layer: Post-processing checks for PII, hallucinations, or policy violations.
- Monitoring Layer: Logging, anomaly detection, and incident response systems.
Adding a “firewall” around the RAG system can further protect against prompt injection attacks and data exfiltration.
Practical Applications of Secure RAG
In all industries, securing RAG applications is necessary for both accuracy and trust. Here are a few ways how it helps:
- Healthcare – provides reliable and validated medical insights while protecting patient data
- Finance – protects sensitive financial information and ensures compliance with regulatory standards
- Legal – helps with secure retrieval of case laws and precedents without risk of manipulation
- Enterprise knowledge management – protects proprietary information as well as boosts employee productivity
- Cybersecurity – enhances threat intelligence systems with secure, tamper-proof knowledge retrieval
How to Implement RAG Application
Organizations looking to implement a secure RAG application can follow these steps:
Step 1: Perform a Compliance Audit
Conduct a detailed audit of the RAG pipeline and ensure that data sources meet the GDPR/CCPA standards and that there is proper data encryption to protect sensitive data at storage.
Step 2: Implement Data Governance Framework
A proper governance policy should be created that covers data minimization, retention timelines, and transparent user data access.
Step 3: Adopt Privacy-by-Design Principles
Integrate data privacy and security measures at all stages of the RAG pipeline, from ingestion to retrieval, by deleting unnecessary personal data and tagging sensitive documents with metadata for informed handling
Step 4: Automate Compliance
Cybersecurity experts can use anonymization tools and compliance APIs like OneTrust or TrustArc, and other security orchestration platforms to automate compliance workflows that can consistently enforce compliance across the pipeline
Final Takeaways
RAG applications combine the capabilities of LLMs with dynamic knowledge retrieval to become a very powerful technology. But these do not come without security risks and challenges, including prompt injection and data leakage.
Organizations must therefore adopt multi-layered defenses like access control, data encryption, input/output filtering, knowledge base vetting, etc., to build trust and resilience. Moreover, effort should be made to balance performance with security.
With comprehensive Cybersecurity certifications from the United States Cybersecurity Institute (USCSI®), cybersecurity professionals can learn the intricate concepts required to secure RAG applications and AI agents at each stage.
The course emphasizes the fact that securing RAG is not a one-time task but a continuous effort. Therefore, organizations looking to keep their data safe and RAG systems reliable and trustworthy must embed security from design to deployment.





