

Shadow APIs Explained: Risks, Detection, and Protection
APIs or Application Programming Interfaces have become the backbone of modern applications in today’s digital business environment. They help organizations offer a seamless user experience and integrate services efficiently.
However, as the development cycles are becoming faster and there is a rise in adoption of microservices and third-party integration, Shadow APIs are growing as the new hidden threat faced by many organizations.
Did you know, a Q1 2025 report reveals 99% of organizations experienced at least one API security incident in the prior year, with injection attacks and Broken Object Level Authorization (BOLA) comprising over one-third of these issues. (Source: Salt Security)
These are nothing but undocumented and unmanaged or often forgotten APIs that bypass security measures and create blind spots for organizations. Therefore, today it has become a major responsibility for CISOs, cybersecurity specialists, and cybersecurity leaders to understand and manage them.
In this article, let us explore what Shadow APIs are, why they are becoming a growing concern, and how cybersecurity professionals can discover and manage them.
What are Shadow APIs?
Any API that is working outside an organization’s documented and monitored inventory is called a Shadow API. Just like ‘shadow IT’, that are unauthorized software and devices, shadow API are also something that developers may deploy without proper authorization and security oversight. Shadow APIs arise from:
- Forgotten leftovers from development and testing
- Rejected endpoints that were never fully decommissioned
- APIs exposed by third-party integrations
- Poor visibility due to fast-paced DevOps practices
The risk of shadow API is simple: if security teams don’t know an API exists, then they cannot secure it. Thus, Shadow APIs serve as the perfect entry point for cybercriminals.
Why Shadow APIs are a Growing Threat?
According to leading cybersecurity tools providers, APIs account for over 80% of web traffic, which makes them prime targets for cyber-attacks. Since there is no proper security of such APIs, they increase the overall attack surface and make the security process even more complex.
Here are some Shadow API risks to be cautious of:
- Since shadow APIs do not have the necessary authentication and authorization, and they lack proper security oversight, they can expose sensitive data
- Shadow APIs handle sensitive data without governance, and thus, they violate regulatory compliance like GDPR, HIPAA, etc., which can lead to legal consequences.
- Attackers are always actively looking for such APIs as they are easy to crack and exploit because of no monitoring and patching
- If there is a security breach because of the Shadow API, then it can lead to service outages, financial loss, and even huge reputational damage.
Cybersecurity leaders and CISOs, therefore, cannot ignore Shadow API in their organizations anymore, and addressing it should be their priority.
Why are Shadow APIs and AI a Double-Edged Sword?
Organizations are now actively adopting AI tools and Agentic AI solutions to enhance their business processes. Though these advanced technologies are helping businesses grow, they make API security more complex.
AI models need to be integrated through APIs for continuous data exchange and decision-making. But if those are shadow APIs, then organizations are at risk of exposing sensitive information.
Moreover, where employees use unauthorized AI applications often rely on APIs to function, which creates parallel risks where unmanaged APIs and AI systems intersect and amplify security blind spots.
Organizations today, hence, combine AI security practices with API monitoring for efficient detection of malicious/anomalous traffic patterns and detect undocumented endpoints in real time.
How to Discover Shadow APIs?
Since you can’t protect what you can’t see, discovering Shadow API becomes the first and most important step in eliminating these vulnerabilities. Here are a few steps to discover Shadow APIs:
- By using automated discovery tools
Today’s advanced cybersecurity tools utilize AI and machine learning to analyze traffic and detect API calls that do not match the documented inventory. These solutions can scan all the infrastructure, including cloud environments, gateways, and network traffic, to detect shadow endpoints.
- API Inventory and Documentation Audits
Organizations also need to have a centralized API inventory. They can flag missing or unregistered APIs by matching the traffic logs with the documented API catalog.
- Network Traffic Monitoring
By monitoring the API traffic and inspecting deep packet, cybersecurity specialists can identify unusual and undocumented endpoints. Monitoring helps identify patterns like deprecated versions that are still receiving traffic.
- Penetration testing
The most effective way to discover Shadow APIs is by hiring penetration testers to detect these vulnerabilities through ethical hacking methods before real hackers find and exploit them.
- Collaboration with Developers
Since developers mostly deploy APIs quickly to meet business needs on time, having regular communication will ensure that all endpoints are registered and properly governed.
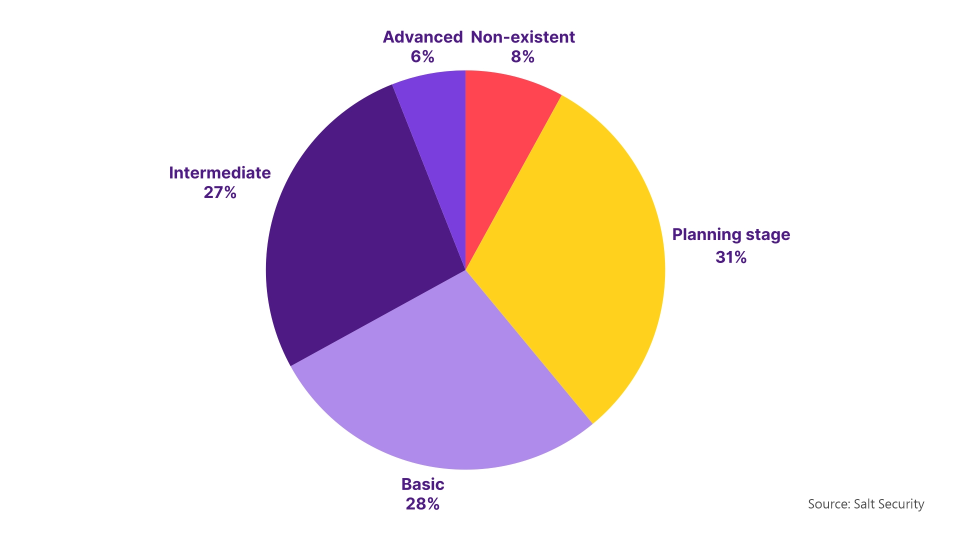
Only 7.5% of organizations classify their API security programs as advanced, meaning the overwhelming majority still face critical gaps. With modern API threats evolving far beyond what traditional defenses can handle, organizations must urgently strengthen their security strategies to reduce vulnerabilities and prevent costly breaches. (Source: Salt Security)
How to Manage Shadow APIs?
Discovery is only half the battle. Effective management ensures Shadow APIs do not appear again or pose a new risk. Some of the best practices to manage Shadow API risks are:
- Implement API Governance Frameworks
Organizations must establish clear policies that necessitate all APIs to be registered and documented, which should be reviewed by security teams before deployment.
- Adopt Zero Trust Principles
Every API must be treated as not trustworthy by default. Organizations should enforce strong authentication, authorization, and encryption policies for all endpoints.
- Use API Gateways
API gateways basically serve as checkpoints and ensure only approved and documented APIs are accessible. These gateways also come with logging and monitoring features to keep a check on various types of APIs.
- Lifecycle Management
Every API needs to have an owner and follow the lifecycle of development, testing, deployment, monitoring, and decommissioning. This will help to dispose of unused or deprecated APIs promptly.
- Continuous Monitoring with AI Security Tools
AI-powered anomaly detection tools can easily identify suspicious or unusual API usage patterns. This will help detect both shadow endpoints and malicious activity effectively.
Role of CISOs and Cybersecurity Leaders
CISOs must balance innovation with security to effectively manage Shadow APIs. While it is a must for developers to focus on agility, CISOs should also enforce governance to ensure APIs don’t become a security threat.
Key responsibilities of CISOs in this matter include:
- Setting up enterprise-wide API security policies
- Investing in effective cybersecurity tools to automate discovery and monitoring
- Offering cybersecurity certifications and training to bring cultural change in the organization
- Properly addressing shadow API risks where unmanaged APIs power unauthorized AI use.
Ultimately, strong leadership, collaboration, and cybersecurity training are important for effective API security.
How to Build Resilience Against Shadow APIs?
By addressing Shadow API issues, organizations not only reduce risks but also build a robust defense against future threats. They must integrate AI security tools, adopt zero-trust frameworks, and ensure continuous visibility so that they can effectively manage their growing API ecosystems.
Also, those individuals looking to succeed in this field should invest in USCSI’s cybersecurity leadership certifications or cybersecurity specialist certifications to gain the essential cybersecurity skills and knowledge required to tackle Shadow API or any other emerging cyber threats.
Conclusion
We live in a world where APIs are driving digital transformation. In this environment, Shadow APIs are one of the most overlooked vulnerabilities. Since they are not paid due attention, they become a more attractive target for attackers.
The priority for CISOs, cybersecurity leaders, and specialists is clear: to discover, document, and defend. They must properly utilize cybersecurity tools, AI security solutions, and strong governance frameworks to ensure Shadow APIs don’t become a threat.
Moreover, by labeling the Shadow APIs a critical issue and providing required training and certifications to the concerned professionals, organizations can keep themselves protected from this growing threat.





