
What are Social Engineering Attacks and How to Protect Against Them?
The greatest cybersecurity threats in this highly interconnected world often do not come from vulnerabilities in any software or applications, but from manipulating people’s trust.
Social engineering attacks are increasing rapidly. They exploit human psychology, bypass technical defenses, and use an individual as a tool to breach an organization’s security, all without their knowledge.
With attackers increasingly integrating AI into their attack tactics, social engineering attacks are increasing both in scale and sophistication. In this article, we will explore what these social engineering attacks are, how they work, how they are evolving with AI, and more. Whether you are looking to start a career in Cybersecurity or are already a cybersecurity specialist wanting to deepen your knowledge on these advanced attack tactics, this is a perfect read for you.
What is Social Engineering?
Social engineering is a broad and widely used form of cyber-attack where the criminals try to manipulate or deceive humans to reveal or share confidential information and perform actions that could potentially compromise their own or their organization’s security.
Unlike other attacks, they do not exploit any software bug but exploit cognitive biases, emotional triggers, authority, urgency, or social norms to trick people into bypassing security protocols.
For example, attackers can impersonate themselves as your boss and create a story so that you share any confidential file/information urgently without getting time to do your research.
In essence, social engineering refers to “hacking people” and turning the human factor, i.e., our tendency to trust, help, and react quickly under pressure, to breach security.
Why are Social Engineering Attacks Dangerous?
- Bypass of Technical Controls
We often talk about how, no matter how strong and robust an organization’s security systems are, there are still chances of security breaches. One reason is this human factor.
Social engineering targets human behavior and, therefore, even strong technical defenses like firewalls, intrusion detection systems, antivirus software, etc., can also be circumvented. If an attacker convinces or tricks someone to hand over a password in some other way, it effectively nullifies the perimeter.
The Chronicle quotes Palo Alto reporting that 36% of incident response (IR) cases in 2025 originated from human manipulated-social engineering attacks as the initial access vector.
- High ROI, Low Effort
Social engineering attacks require a very minimal infrastructure. Attackers can do this with the help of only an email account, a spoofed caller ID, or a voice-cloning tool. It can, of course, scale with more resources and tools. As highlighted by Palo Alto, attackers use AI to accelerate impersonation campaigns and dialogue-based tactics that make attacks look highly realistic and reduce overhead.
- Dwell time and lateral movement.
After the attackers gain access, they can move laterally inside networks, exploit data, escalate privileges, and almost do anything. In social engineering attacks, breach looks like legitimate behavior (example – a user logged in from the organization’s legitimate device/machine), and because of this, incidents often go unnoticed.
- Emotional leverage and urgency
Social engineering does not give users time to think and work by cutting off deliberation. Attackers appeal to fear, authority, urgency, and desire to help. These emotional triggers are more powerful than vulnerabilities in code.
- Adaptability
Attackers can also change their lures rapidly. They can customize emails for new events or news. They can mimic ongoing crises and even combine vectors like emails with voices. By leveraging AI, they can adapt to any situation dramatically faster.
How and Why Social Engineering Works?
By breaking down the process and psychological underpinnings, we can understand the working mechanics of social engineering attacks in a better way.
The image below shows different stages of the social engineering attack cycle. It has been explained further below.
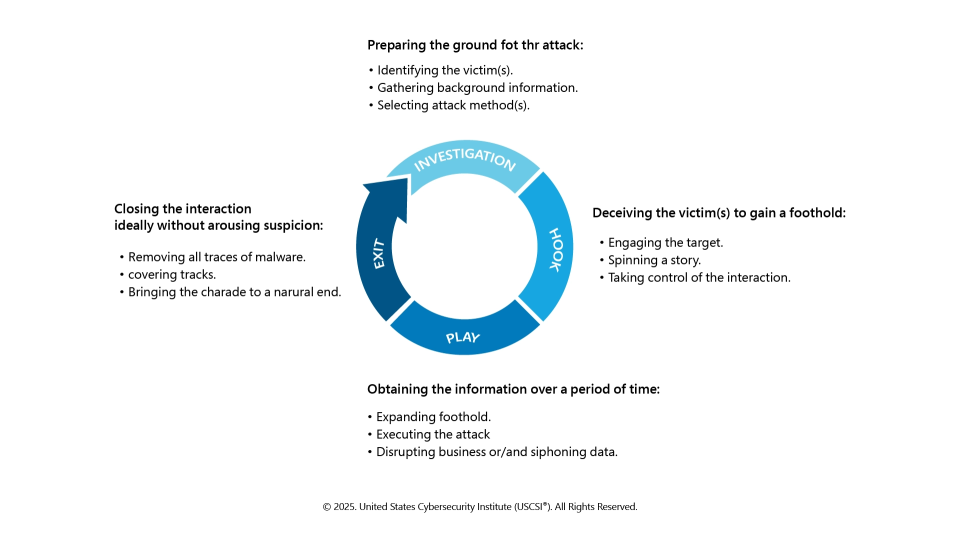
Understanding The “Social Engineering Life Cycle”
- Reconnaissance: Information Gathering
It all starts by gathering essential information about the target, like their job title, colleagues, recent events, social media, published contact info, etc. The more data attackers have, the more convincing the approach will be.
- Pretext: Crafting the Narrative
The attackers then build a justification – for example, “I’m from your IT team”, “Your invoice failed”, “We have a security alert”, etc., that gives credibility to the request.
- Engagement: Interaction
Next, the attackers approach the target by email, phone, chat, or even in person (sometimes). They push the target to perform immediate actions like clicking a link, opening an attachment, revealing a password, installing remote access, transferring funds, etc.
- Exploitation: Execution
The victim complies (or partially complies), giving access. Attackers may escalate from a foothold, pivot to more sensitive systems, or exfiltrate data.
- Covering Tracks: Persistence
Often, attackers try to cover up their actions and maintain persistence (e.g., via backdoors) to return later.
Psychological Principles Exploited
In social engineering attacks, the following psychological principles are exploited:
- Authority - People tend to obey perceived authority figures. If someone claims to be your CISO, your bank, or your manager, you are more likely to comply
- Reciprocity – Attackers can offer something like help or compensation in exchange for cooperation
- Urgency – creating a time pressure that prevents reflection
- Social proof/consensus - Attackers can say “everyone else already did this” or reference peer behavior
- Liking/ flattery – they also compliment or demonstrate friendly behavior that hinders defenses
- Scarcity/fear - in this, the threat of loss pushes rapid compliance
Social engineering attacks mostly work because these manipulations tap into cognitive shortcuts. Therefore, even most security-savvy professionals can also easily fall prey to such attacks, especially under pressure. With proper cybersecurity training and cybersecurity certifications, organizations can increase awareness among all employees.
Notable Social Engineering Incidents to Reflect Upon
Now, let us reflect upon some of the social engineering incidents:
- ClickFix
In 2025, LevelBlue’s Threat Trends report observed that social engineering accounted for 39% of initial access incidents, driven largely by a 1,450 % surge in “ClickFix” fake CAPTCHA campaigns. These hijack users into running malicious scripts under the guise of solving a CAPTCHA.
- Phishing amplified by AI
Hoxhunt reports that an AI-driven phishing agent between 2023 and 2025 improved its effectiveness relative to human red teams by 55 %, and by 2025, such agents outperformed humans across user skill levels.
- Deepfake voice impersonation
Adversaries now clone executive voices to call employees and request fund transfers or credentials. The Palo Alto Unit 42 data indicates that AI-driven impersonation is a growing tool in social engineering intrusions.
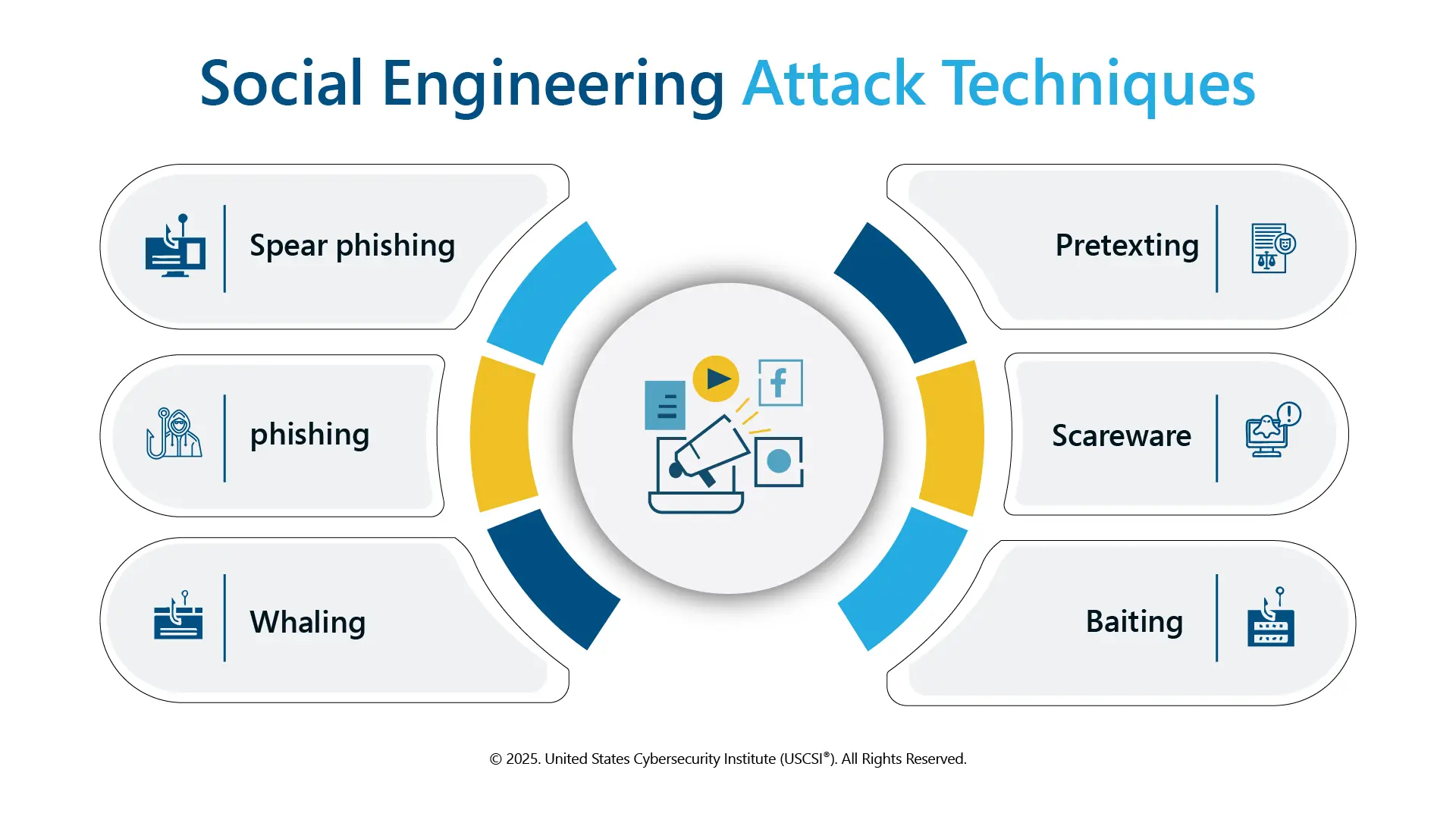
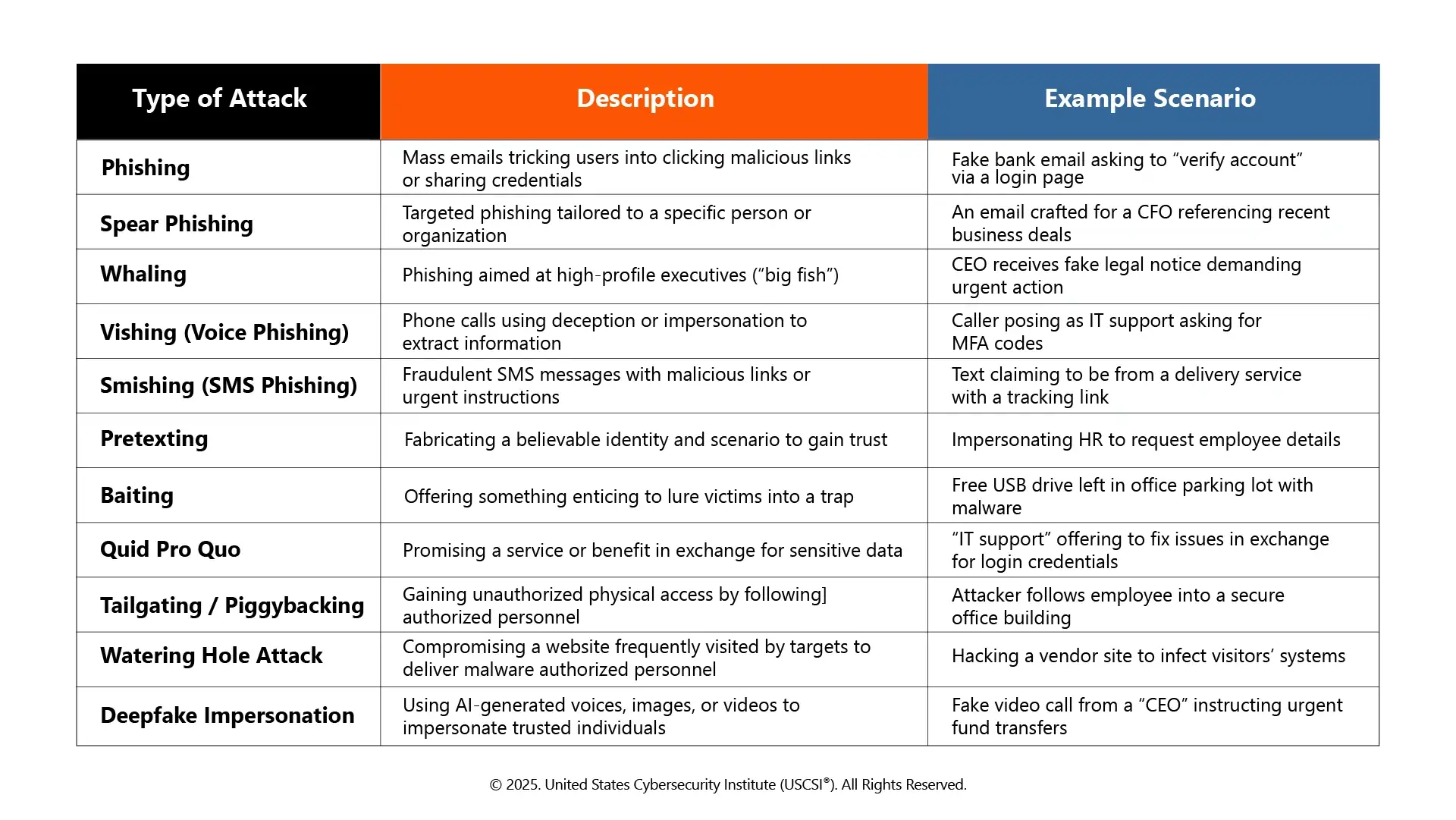
Types of Social Engineering Attacks
There are various tactics involved in social engineering attacks. Some of the common types, along with their example, are explained below:
Social Engineering Defenses and Prevention
Now, let us explore the best mitigation and prevention strategies for social engineering attacks, an approach that combines all people, processes, and technology.
- Security Awareness and Training
Conduct regular cybersecurity training and awareness programs for employees across departments to teach them how to recognize social engineering tactics. Employees must always question if they receive unexpected requests for credentials or fund transfers and validate them. They should be trained to spot red flags like – mismatched email domains, urgency, unexpected attachments, incorrect grammar, or tone.
- Least-Privilege and Zero Trust Principles
This means granting only necessary access to users and using just-in-time privileges. Organizations should also adopt Zero Trust security to verify all requests continuously. This will limit attack surfaces and reduce risks from compromised accounts.
- Multifactor Authentication (MFA) and Adaptive Authentication
MFA is a great way to add an additional layer of security beyond passwords, and adaptive authentication helps enforce a stronger check against unusual logins. Combined together, they can significantly reduce the theft risks of passwords and credentials.
- Behavioral Analytics and Identity Threat Detection
UEBA and ITDR tools can be used to detect abnormal user behavior and anomalies to detect threats. It also helps to monitor misuse and assists with faster lateral movement for proactive incident response.
- Network and Endpoint Controls
Advanced network security systems like email filtering, domain reputation checks, URL filtering, etc., should be employed to block malicious lures. Moreover, using DNS security and web proxy controls can help block access to suspicious domains. EDR tools can detect suspicious processes triggered by malicious links or attachments at endpoints.
- Segmentation and Control of Privileged Credentials
Segmentation of networks can help prevent lateral movement of the attackers and eliminate compromised user accounts from pivoting to critical systems. Also, it is recommended to use isolated “jump hosts” or bastion servers for administrative work.
- Using AI for Defense
Cybersecurity professionals must leverage AI and machine learning systems to detect anomalies in communication, flag suspicious emails, and detect deepfake voices. Generative AI can also be used to simulate phishing attacks and train employees on emerging tactics.
Role of AI in Social Engineering Attacks
Artificial intelligence in cybersecurity, since the start, has been termed as a dual-edged sword. It powers both the attack and defense of social engineering attacks. When we talk about the offensive side, generative AI can help attackers create highly customized phishing emails, realistic voice and video deepfakes, and even manipulate organizational chatbots to leak sensitive information.
Phishing campaigns distributing info-stealers saw an 84% increase in weekly delivery rates (Source: IBM). Today, the cost of phishing campaigns has dropped drastically, but their effectiveness has increased significantly as autonomous phishing AI agents can perform better than human red teams. The Gigamon Survey indicates that there is a 59% rise in AI-powered social engineering, smishing, and phishing campaigns.
Emerging AI-driven threats are taking social engineering to new levels. Techniques like vibe hacking exploit emotional cues to manipulate trust, while prompt hacking targets AI systems by injecting malicious instructions to override safeguards. Understanding these evolving attack vectors is crucial for building stronger defenses in today’s cybersecurity landscape.
At the same time, AI can be a great savior. AI-powered threat detection systems can flag deepfakes, unusual communication patterns, and anomalies early with higher accuracy. Moreover, leveraging AI-powered training simulations can also prepare employees to protect against evolving and emerging cyberthreats. Augmented threat intelligence can also enhance visibility across networks, email, and endpoints. Most importantly, by integrating AI into zero-trust frameworks and access controls, organizations can add another layer of security for enhanced protection.
However, organizations should be aware that attackers can also employ adversarial AI techniques, including model poisoning and evasion, and therefore, they require continuous monitoring and training.
The final thoughts!
Social engineering is a critical cybersecurity risk. Since it exploits human trust, it is free from the robust technical measures organizations implement. Moreover, AI is making such attacks more powerful, scalable, and highly convincing. Therefore, organizations must adopt modern defense techniques and use AI-powered detection, behavioral analytics, Zero Trust Architecture, strong identity controls, etc.
With USCSI® certifications, organizations and professionals can master the latest tools and techniques needed to thwart even the most sophisticated and powerful attacks, like AI-powered social engineering attacks. Organizations must partner with USCSI® to offer world-class cybersecurity training and awareness to their employees and reinforce their strong security by securing their people. As a professional, you can enroll in the best cybersecurity certification programs from USCSI® and take your career forward in 2026.





