Kerberos: What is it and How Does it Work?
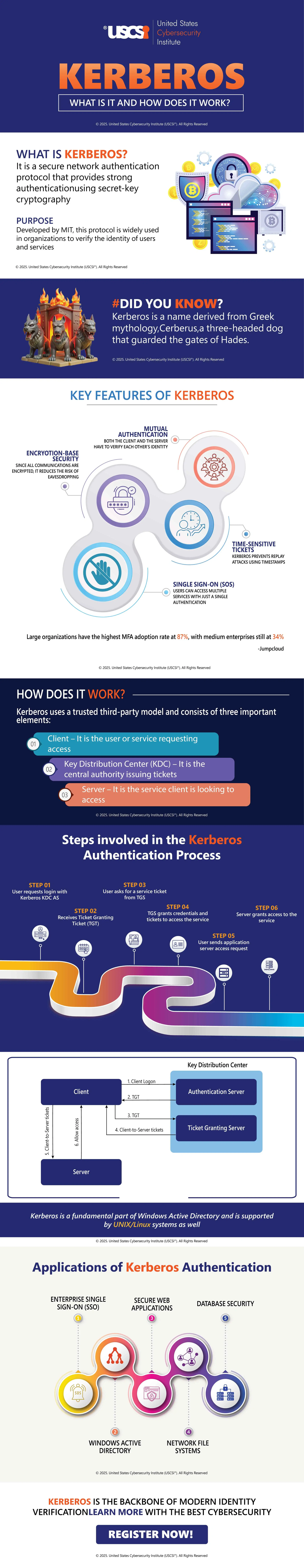
The importance of secure authentication is larger than ever, and in this aspect, Kerberos stands out as a time-tested network authentication protocol, helping enterprises verify user and client identity for secure communication.
In our latest infographic below, we elaborate on the essentials of Kerberos authentication in a clear and visually appealing format, perfect for all IT professionals, enthusiasts, as well as cybersecurity specialists.
IBM’s latest report highlighted how 36% of data breaches involved attackers using valid credentials. This indicates how important the Kerberos authentication protocol has become to secure such online communications.
Developed by MIT, this protocol uses secret-key cryptography and a trusted third-party model called Key Distribution Center (KDC) for secure authentication and access to the service. This technology also powers Single Sign-On (SSO), where you can just log in once and access multiple systems securely.
So, check out the following infographic and learn about the key features of Kerberos, its 6-step authentication flow (from login request to service access), its applications such as Windows Active Directory, secure web pages, symmetric cryptography, and more. Also, consider reinforcing your cybersecurity skills and knowledge about Kerberos with top cybersecurity certifications from USCSI® for a rewarding career ahead.
Check out the infographic guide below and see how Kerberos can keep your network safe and efficient.