

A Detailed Dive into Message Authentication Codes (MACs)
With the ever-changing digital landscape and a commitment to data protection, Message Authentication Codes (MACs) have developed into critical elements for supporting message integrity and authenticity. We are threatened with an array of cyberattacks, including spoofing, data tampering, and more, all of which highlight the need to know that exposure on a public interface does not change the information shared. This is where MACs are important.
The IBM Ponemon Report 2025 emphasizes the escalating costs and complexities of data breaches, demanding a proactive and adaptive approach to cybersecurity. The sharp increase demonstrates the need for authentication mechanisms, like MACs, to help limit trust and risk and reduce operational impact.
In this blog, we will discuss what a MAC is and how it works, why it’s important for cybersecurity, the algorithms that apply, as well as best practices that professionals and aspiring cybersecurity professionals should follow..
What is a Message Authentication Code ?
A Message Authentication Code (MAC) is a small amount of information produced from a message and a secret key. It assures both data integrity, determining that the message has not been altered, and data authenticity, verifying who the sender is.
MACs are found in many cybersecurity tools and standards, including SSL/TLS, IPsec, and SSH; they are a building block of secure communications.
While digital signatures use asymmetric key cryptography, MACs use symmetric key cryptographic methods, in that both the sender and receiver have the exact same key for the operational context within which the sender and receiver are operating.
How MAC Works
The MAC generation and verification can be described as follows:
- Input: Message and a secret key.
- Processing: The message is run through a MAC algorithm that may use a hash function, a cipher, or a different type of mathematical function.
- Output: A fixed-length MAC value, or tag.
- Verification: The receiver generates their own MAC using the same secret key and algorithm and compares it with their received MAC. If both MACs are the same, the message is authentic and there is no tampering.
Real-World Analogy
Consider a MAC as an envelope's wax seal. The seal (MAC) makes sure the data hasn't been opened or altered before it reaches the recipient, while the message within is kept secret.
MAC Algorithms and Hash Functions
Today, several MAC algorithms are in use, the majority of which rely on block ciphers or underlying cryptographic hash functions.
Common MAC Algorithms:
- HMAC (Hash-Based Message Authentication Code)
- Employs a hash function in cryptography, such as SHA-256.
- Most extensively used because of its effectiveness and simplicity.
- Present in the protocols TLS, HTTPS, and IPsec.
- Cipher-Based Message Authentication Code
- Based on AES and other block ciphers.
- Better suited for settings where encryption algorithms are already in use.
- Utilized in embedded and military-grade systems.
- UMAC/VMAC
- Concentrate on performance and speed.
- Built for environments with high-throughput authentication needs.
All of these algorithms have an important place in today's cybersecurity infrastructure, and authentication must be reliable and efficient.
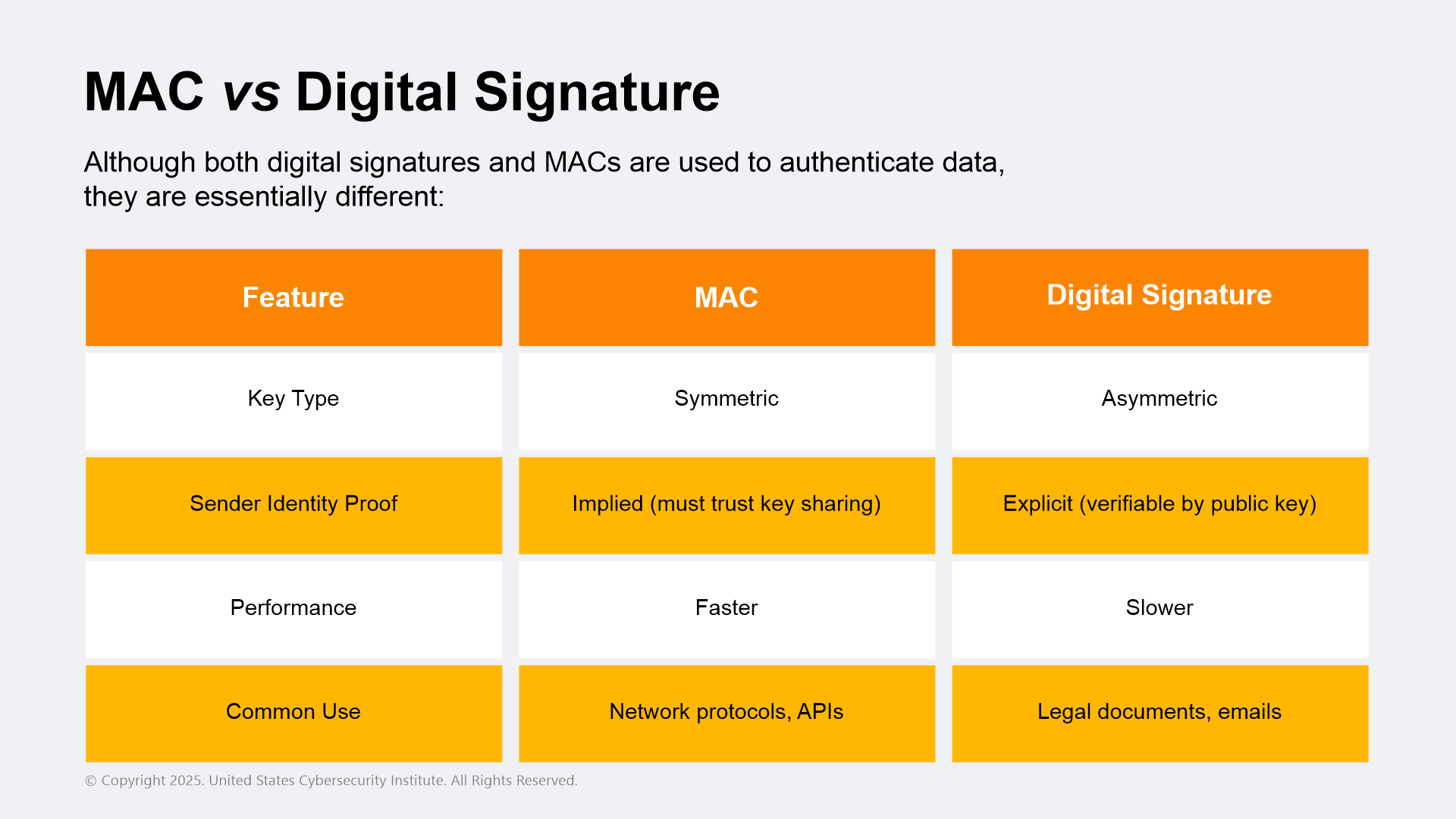
Digital signatures are the best option when non-repudiation is crucial, while MACs are the preferred choice for real-time and performance-critical systems.
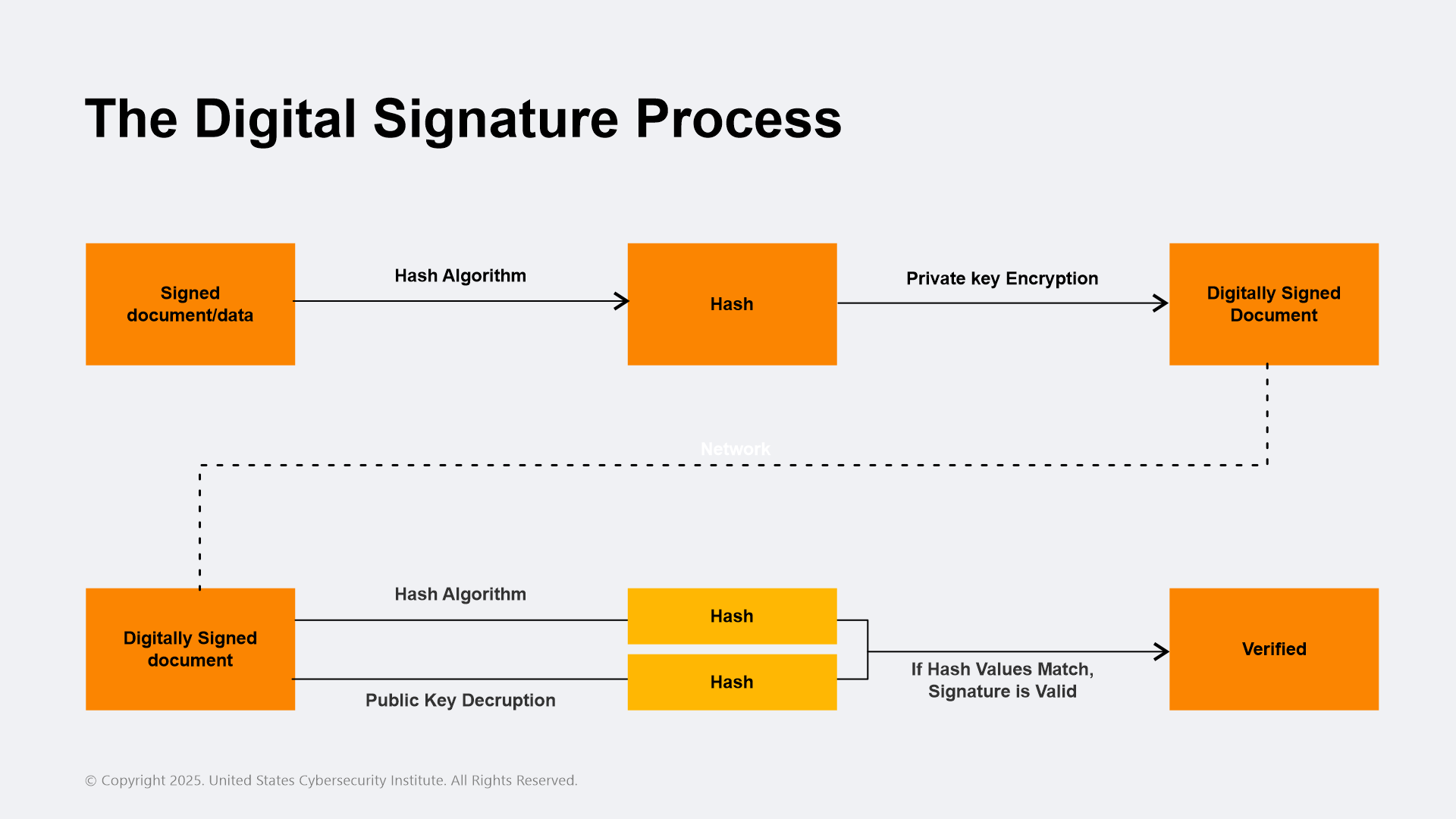
Why MACs Are Important for Cybersecurity Professionals
When it comes to cybersecurity professionals, there is no bigger need to understand MACs. Their use is widespread in the realms of authentication, data validation, and ensuring protocol security. If you are designing secure APIs with authentication, if you are managing encrypted sessions, and if you are in the world of penetration testing, then a MAC is the underlying basis of the security you trust.
Professionals who hope to progress as cybersecurity professionals should have a good understanding of the practical application of MACs, the distinctions between symmetric and asymmetric cryptography, and the benefits and potential downsides of various MAC algorithms.
Best Practices for Using MACs
- Use Strong Keys
Keys should be high in entropy, using a length that would take too long to compare with brute force, like 256 bits.
- Use Trusted Algorithms
Do not use old, insecure MACs like MD5 and HMAC; trust modern standards. Rely upon HMAC-SHA-256 and CMAC-AES.
- Use Proper Key Management
You must be able to store symmetric keys securely, rotate them, and ensure only authorized users can access them.
- Do not Use the Same Keys in Multiple Systems
Are lots of keys in play here, even if multiple systems are just guessing the traffic at a few hash algorithm sequences? The chances of replay attacks or cross-protocol attacks are higher using the same key.
- Use Authentication on Every Message
Always authenticate every incoming message or data, even if the incoming message is over an untrusted network.
- Combine with Encryption
MACs only provide authentication and not confidentiality. Proper use of MACs means that you would also use encryption to provide confidentiality. Encryption, for example, can be AES.
Strengthening Your Cybersecurity Career with MAC
It's not enough to know the theory underlying the Message Authentication Code (MAC); rather, you must learn to implement one of the most important building blocks for protecting data. As the threats to cybersecurity evolve, experts trained in cryptographic algorithms and a deep understanding of MACs are highly sought after.
If you are an aspiring learner or practitioner seeking to grow, USCSI® has specialized cybersecurity certifications designed by industry experts. Their courses include advanced cryptography, ethical hacking, and essential tools used in cybersecurity, an experience tailored to those who want to launch or grow a successful cybersecurity career.





