

Must-Have Cybersecurity Tools for 2026
As cyber threats develop, organizations and individuals are faced with increasingly complex attacks. The average cost of a data breach for U.S. companies hit a record of $10.22 million in 2025, according to IBM's Cost of a Data Breach Report.
This reinforces our need for advanced cybersecurity capabilities and proactive defense. Since hybrid work, cloud adoption, and AI-driven threats are the new normal, it is no longer sufficient to have legacy security capabilities in place.
In this blog, we look at what you need to know about the top cybersecurity tools available for 2026. We will explore endpoint protection, threat intelligence platforms, AI technologies, and more to help organizations stay resilient against ransomware and data breaches and continue to address continuous, modern cybersecurity risks.
1. Endpoint Detection and Response (EDR) Systems
EDR tools are designed to run on computers, servers, and mobile devices to observe these endpoints for suspicious activities. The tools can identify and isolate infected endpoints before the inferior code spreads. By 2026, EDR systems will leverage machine learning and behavioral analytics to identify unknown threats, automate response actions, and ultimately prevent ransomware attacks before they occur. EDR tools are invaluable within a hybrid work environment, where endpoints are typically the weakest link.
- CrowdStrike Falcon Insight: Delivers ongoing endpoint monitoring utilizing artificial intelligence and machine learning capabilities. It detects malware, ransomware, and fileless attacks while automatically isolating or confining infected devices. It also provides detailed forensic reports that assist organizations in understanding its attacking vectors.
- SentinelOne Singularity: Utilizes autonomous AI to monitor endpoint behavior and detect anomalies. It has the capability to rollback compromised systems, prevent the spread of ransomware, and provide automated remediation for zero-day attacks.
2. Extended Detection and Response (XDR) Platforms
In 2026, Extended Detection and Response platforms will be instrumental for organizations handling complicated infrastructures. By combining data from endpoints, networks, email, identity solutions, and the cloud, XDR platforms provide a single pane view of possible threats. Some of the popular tools are:
- Microsoft Defender XDR: Integrates signals from endpoints, Office 365, and Azure to create full visibility and automated remediation workflows. On top of that it uses machine learning to help prioritize alert triage to significantly reduce incident fatigue for SOC.
- Trend Micro Vision One: Provides cross-layered threat detection across endpoints, email and collaboration (e.g., O365), servers, and cloud workloads. The advanced analytics can detect multi-stage attacks early and support automated playbooks to leverage rapid containment capabilities.
3. Security Information and Event Management (SIEM) Tools
By 2026, Security Information and Event Management (SIEM) tools will use cloud-native architectures and AI-driven analytics to detect anomalies, automate alert triage, and streamline the incident response process. They will be critical for compliance reporting, forensic analysis, and real-time monitoring across complex enterprise environments.
The tools are:
- Elastic Security: A scalable SIEM platform that incorporates threat detection, investigation and response capabilities in the Elastic Stack to provide visibility and analytics in real-time for hybrid environments.
- Hunters AI-Driven SIEM: An advanced SIEM platform that leverages artificial intelligence to correlate a variety of data sources, detect advanced threats and enable automated investigation workflows.
Those skilled in SIEM are highly valued, according to Glassdoor, the average salary for a SIEM Engineer in the U.S. is around $101K, while senior roles like Detection Engineers or SOC Managers can earn up to $180K annually.
4. Managed Detection and Response (MDR) Services
As cyber threats continue to increase, many organizations are unable to afford a 24/7 in-house security team. Managed Detection and Response services combine technology with human monitoring to facilitate continuous threat hunting, proactive defense, and incident response. They provide enterprise-level protection without the expensive price tag.
The tools are:
- Rapid7: Offers real-time monitoring, AI-enabled embedding detection, and expert direction for containment and remediation. Rapid7 integrates into your existing security infrastructure to enable the security team to respond faster while lowering operational risk.
- Arctic Wolf MDR: A Security Operations Center-as-a-Service, providing around-the-clock monitoring, proactive threat detection, and vulnerability management. Dedicated Security Advisors assist municipalities in strengthening defenses during an incident and responding to advancements in threat scenarios.
Utilizing MDR services results in reducing security incidents, demonstrating the benefits they have on improving cybersecurity.
5. Attack Surface Management (ASM) Tools
As organizations expand their digital footprint through cloud adoption and hybrid infrastructures, it is critical to secure every internet-connected asset. Attack Surface Management tools continuously monitor external assets, identify potential vulnerabilities, and provide insights into shadow IT, exposed APIs, and outdated subdomains to prevent exploitation by attackers.
The tools are:
- CyCognito: Automatically finds and assesses your internet-facing assets, including systems that were hidden. It provides actionable visibility and prioritized remediation steps to minimize your attack surface and to stop a breach before it happens.
- Palo Alto Networks Cortex Xpanse: Continuously maps and monitors an organization’s global attack surface for unknown assets, misconfigurations, and vulnerabilities. It provides risk scoring and recommendations for proactive defense.
These tools enable continuous monitoring, reduce the risks of breaches, and enhance the overall security posture. As per Glassdoor, a Security Technical Architect with specialized knowledge about ASM is projected to make between $75K to $121K annually.
6. Cloud Security and Workload Protection Platforms
As of 2026, businesses are increasingly dependent on cloud computing, making the protection of virtual machines, containers, and serverless workloads essential. Cloud Workload Protection Platforms (CWPPs) safeguard data, enforce access controls, and ensure compliance with standards like ISO 27001 and GDPR, helping organizations secure multi-cloud environments.
The tools are:
- Aqua Security: It focuses on keeping cloud-native and container-based applications secured with runtime protection, vulnerability scanning, and compliance enforcement services. As a security provider, Aqua integrates with CI/CD pipelines to ensure applications are secured from development to production, providing continuous monitoring, and threat prevention.
- Check Point CloudGuard: Delivers real-time workload protection with automated threat prevention, identity-based access controls, and multi-cloud visibility. It ensures compliance and reduces risks of misconfigurations, data leaks, and malware attacks.
The CWPP market is rapidly expanding, estimated at $6.4 billion in 2025 with a 22.1% CAGR, reflecting growing demand for Cloud Security Engineers, DevSecOps, and Cloud Security Architects.
7. Vulnerability Assessment and Penetration Testing Tools
In 2026, scanning systems and simulating attacks is essential to spot weaknesses before hackers do. Vulnerability assessment and penetration testing tools identify misconfigurations, outdated software, and hidden flaws, helping organizations strengthen security proactively.
The tools are:
- Nessus: Assesses networks, systems, and applications for vulnerabilities while providing risk ratings and comprehensive reports to focus on priorities for fixing.
- Burp Suite: Evaluates web applications with vulnerabilities such as SQL injection and XSS using both automated scans and manual tests to ensure protection.
These tools ensure organizations can detect and remediate weaknesses before they are exploited.
8. Threat Intelligence and Analysis Platforms
Threat intelligence platforms assess and collect the vast amount of data produced by malware, phishing attempts, and new attack patterns to help organizations prepare for potential threats before they occur. They provide context for alerts, enabling faster and more effective defense.
The tools are:
- IBM X-Force Exchange allows teams to leverage real time threat intelligence and share information on vulnerabilities, malware, and attack activities. It can also integrate with security systems located on public clouds and behind your enterprise firewall to help facilitate proactive threat response.
- Recorded Future pulls in threat data from a variety of sources and specifies language from the vendor presence in the larger threat intelligence market. Recorded Future combines risk scoring, predictive analytics, and actionable insights to support teams in preventing cyber-attacks before they occur.
As MarketsandMarkets notes in “Threat Intelligence Market – Global Forecast to 2030”, the threat intelligence market is expected to reach $22.97 billion by 2030, showing the rising need for threat intelligence platforms as organizations face more sophisticated cyberattacks.
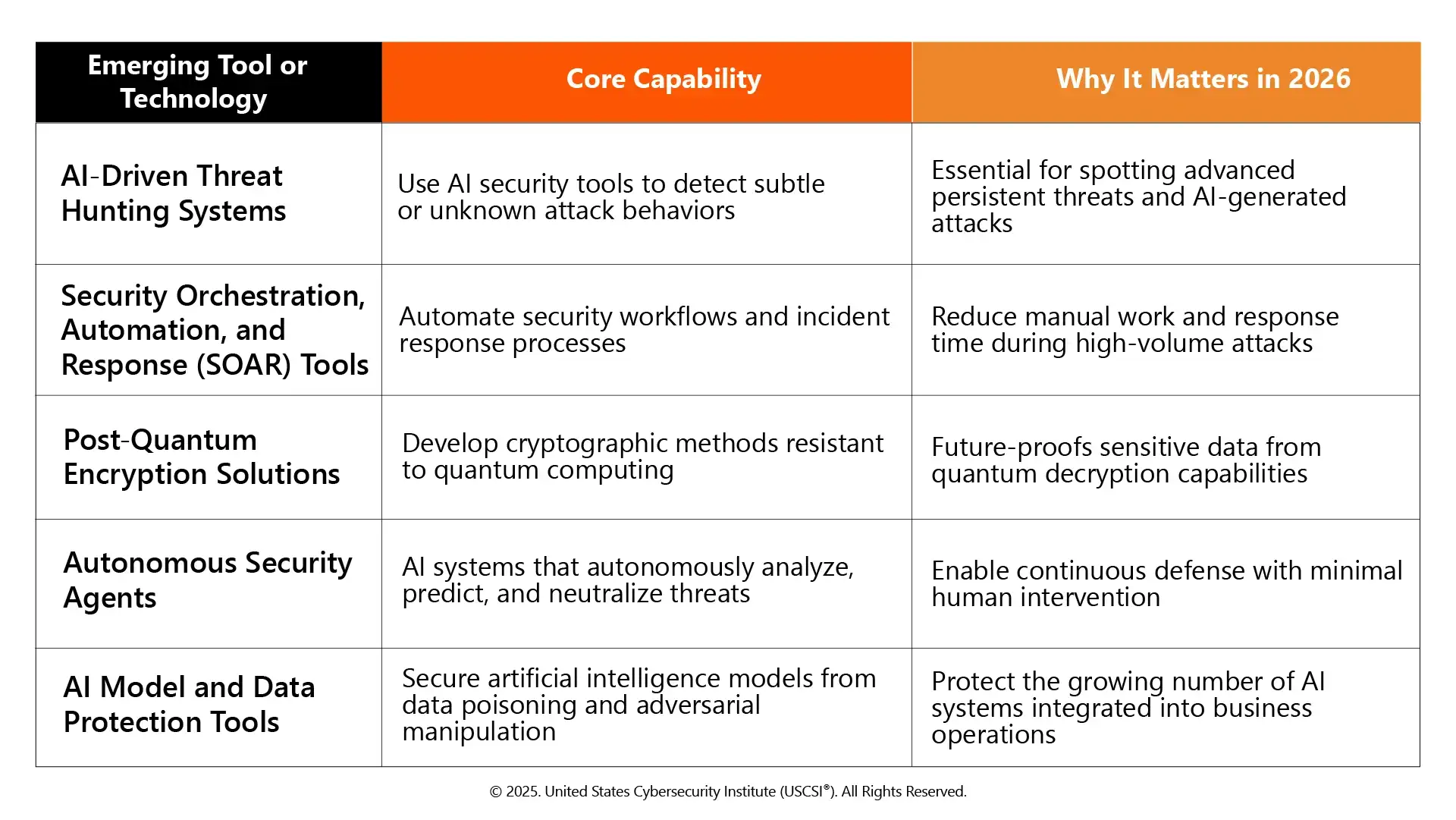
Read More: Top 8 Cybersecurity Trends to Watch Out in 2026
Conclusion
In 2026, cybersecurity needs both smart technology and human intelligence. AI-based threat intelligence is changing the way we defend ourselves in a big way, along with the rise of EDR, SIEM, and Zero Trust security technologies.
Taking advanced cybersecurity training programs from USCSI® can help professionals stay ahead of new cyber threats by gaining required knowledge and skills. Combining smart technology with trained people can help organizations become more resilient and stay ahead of new threats.





