CERT vs CSIRT vs SOC: Understanding Cyber Defense Roles | Infographic
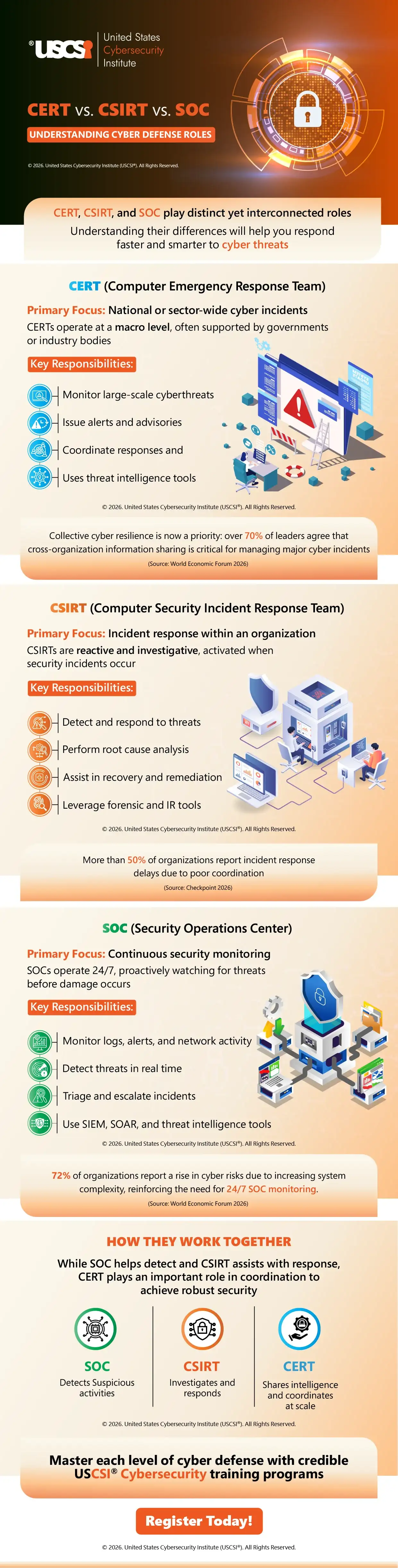
Organizations cannot rely on just one cybersecurity team for all-around protection. Often, in most secure organizations, we can find three types of cybersecurity teams operating to enhance overall security, namely SOC, CSIRT, and CERT.
They have different functions, but the goal is the same – improving cyber resilience.
A Security Operations Center (SOC) is considered the frontline defense. It works 24/7 to continuously monitor networks, analyze alerts, and detect suspicious activities in real time. Their focus is on identifying threats earlier and rapid containment, before damage spreads.
A Computer Security Incident Response Team (CSIRT) starts working when an incident is detected. They investigate the attack, contain the threat, minimize the damage, do digital forensic analysis, and manage disaster recovery efforts. CSIRT team ensures business continuity with prompt incident response with minimal impact.
Over 70% of leaders believe knowledge sharing is important for incident management (Source: WEF Report). This finally brings in the importance of the Computer Emergency Response Team (CERT), who operate at a much broader level. CERTs mostly function at the national, sectoral, or industry level, and their core function is to issue alerts or share threat intelligence. They coordinate responses across multiple organizations.
In short, SOC detects, CSIRT responds, and CERT coordinates. The infographic below gives a detailed overview of these three. With USCSI® cybersecurity certifications, learn more about these cybersecurity techniques and elevate your career prospects in the industry.