
Information Technology (IT) vs. Operational Technology (OT): A Cybersecurity Comparison
Organizations are increasingly deploying smart infrastructure and automation, which means the convergence of information technology (IT) and operational technology (OT) environments will introduce new security risks across both digital and physical environments.
As reported by Fortinet's 2025 OT Security Report, 52% of organizations have placed OT cybersecurity under the responsibility of the CISO, and 46% of organizations report that they have achieved Level 4 OT maturity, with a deliberate focus on uptime, reliability, and industrial resilience.
While, according to Fortinet's 2025 Global Threat Landscape Report, stolen credentials shot up 42% year-over-year and exploitation attempts occurred more than 97 billion times, demonstrating how automated AI-driven attacks target data-rich IT systems.
Although IT and OT security teams are attempting to protect critical infrastructure for similar objectives, there are significant differences in the assets, risk tolerance, and operational conditions between IT and OT teams.
The continuing evolution of the Internet of Things (IoT) is resulting in blurring the lines between these two worlds; however, to ensure an effective way to protect the operational fabric that powers both digital and physical operations, understanding and analyzing the respective nuances and intersection points of IT and OT cybersecurity are critical.
Understanding Information Technology (IT)
Information technology concerns itself with systems designed to process, communicate, and store data. This includes servers, networks, cloud platforms, applications, and databases.
The goals of cybersecurity in an IT context include
Confidentiality: Securing sensitive data
Integrity: Ensuring data is valid and unchanged
Availability: Ensuring data and applications can be accessed
IT cybersecurity typically involves protection from malware, phishing, data breaches, and insider threats, with common defenses including encryption, firewalls, antivirus software, and patching.
IT systems are articulated to be dynamic, scalable, and highly adaptive to updates. In contrast to OT, downtimes in IT, whether for maintenance periods or security patch processes, are usually less disruptive and acceptable.
Understanding Operational Technology (OT)
Operational technology encompasses hardware and software systems that perform monitoring and control on physical processes such as power grids, oil pipelines, ICS, PLC, SCADA, and HVAC systems.
Unlike IT, where the existence of data is paramount, OT systems focus on:
- Availability: Systems must always be ON
- Safety: No injuries or fatalities can happen
- Reliability: Your operations can not be interrupted
Historically, operational technology systems were completely isolated from the Internet and any networks for security purposes; however, with the advent of smart manufacturing and Industrial IoT (IIoT), these systems are now interconnected and increasingly subject to cyber risks that similarly challenge IT systems with even greater degrees of risk in reality.
IT Security vs OT Security: Comparative Analysis
Though both IT and OT require protection, they differ in critical ways:
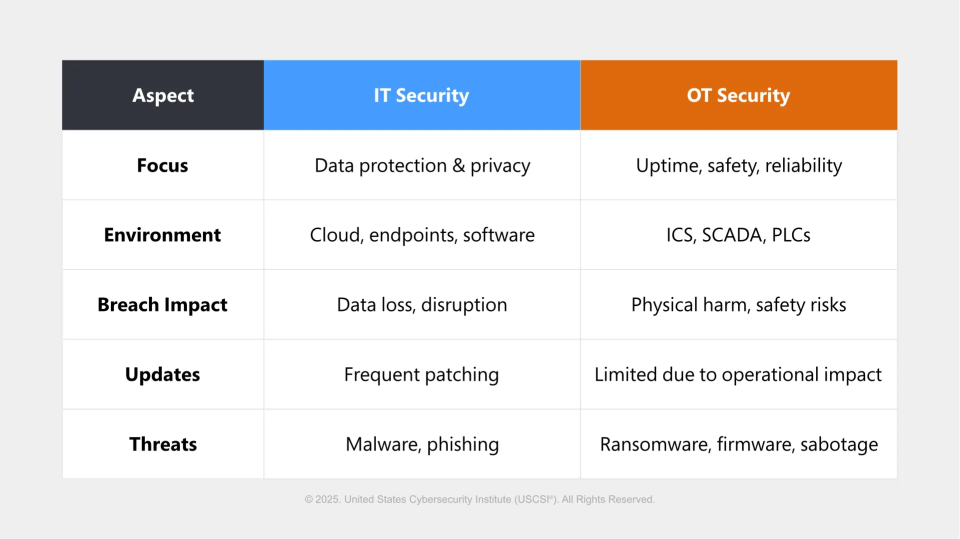
These differences mean traditional IT tools often don’t work in OT environments, and vice versa.
Similarities Between IT and OT Cybersecurity
Despite the contrast, IT and OT security do overlap in several areas:
- Both require network segmentation and access control
- Both need real-time monitoring and threat detection
- Both benefit from zero trust architecture
- Both depend on skilled professionals and formal incident response plans
- Both are increasingly affected by IoT devices and remote connectivity
As convergence accelerates, cybersecurity expert teams should create a single risk management framework that simultaneously accommodates both areas.
Why IT and OT Collaboration Is Necessary
With the adoption of smart systems and cloud platforms into enterprise processes, the distinction between IT and OT is disappearing. Many events now originate from IT and spread into OT (or vice versa), meaning a breach in one environment can impact the entire environment.
To provide protections for both environments, organizations must:
- Unify monitoring across the IT and OT networks
- Enable cross-team collaborative incident response
- Utilize platforms that provide shared visibility and threat intelligence
OT cannot afford to be isolated any longer. Collaboration is not an option; it is a requirement.
The Role of IoT and IIoT
The Internet of Things (IoT) and Industrial Internet of Things (IIoT) are fundamentally shaping the info tech/operational tech convergence, but they also introduce significant security vulnerabilities.
IoT devices often contain
- By default, low-strength credentials
- Little to no frequency of receiving security patches
- Limited processing power for actual cybersecurity tools
Because of these flaws, attackers target IoT devices, which, once compromised, can:
- Access corporate IT networks
- Modify OT control systems
- Launch botnet DDoS attacks
To mitigate the risk of IoT-to-OT threats and attacks, security teams will need to invent every connected device, isolate IoT traffic, and monitor IoT traffic for anomalous activity.
Best Practices Snapshot
To protect both IT and OT systems, the following best practices are recommended:
-
Implement Zero "Trust—"never trust, but always verify," especially in OT networks
-
Segment Networks—Use zones and conduits to separate OT from IT
-
Deploy Behavioral Analytics—Identify anomalies based on OT behaviors
-
Enforce Multi-Factor Authentication—Lower risk for unauthorized access
-
Use integrated security platforms—get centralized visibility and coordinated threat response
Many of these best practices will yield the greatest benefit when adapted to the inherent constraints of OT systems, for example, uptime requirements and acceptable network protocols.
Conclusion
As IT and OT systems become more integrated, the protection of data and physical infrastructure requires a cybersecurity evolution. Threats are advanced, and it will take an integrated approach and skilled cybersecurity professionals with an understanding of both the IT and OT domains. Cybersecurity Certification Programs offered by USCSI® help develop this cross-functional knowledge base. In the future, strong defenses will be gained through not only better tools but also smarter people and the evolving collaboration across IT and OT.





