

Quantum Security Demystified: How It Works and Why It Matters
There is more to protecting sensitive data than creating stronger passwords and smarter firewalls. If organizations want to protect themselves from attackers, quantum threats must be at the front of their minds. Quantum computing can have a serious negative impact on traditional encryption systems, and therefore, organizations should consider committing to quantum security, including governments, enterprises, and cybersecurity professionals.
The quantum security market size has grown exponentially in recent years. It will grow from $1.14 billion in 2024 to $1.7 billion in 2025 at a compound annual growth rate (CAGR) of 49.0%. The growth in the historic period can be attributed to the demand for enhanced simulation and modeling, the increased complexity of automotive systems, the increased focus on cybersecurity, collaborative research initiatives, and regulatory pressure (The Business Research Company).
This blog breaks down what quantum security means and how quantum security works, such as with Post-Quantum Cryptography or Quantum Key Distribution, and most importantly, why cybersecurity professionals must act quickly to follow the path to the post-quantum world.
The Quantum Threat: Why It Matters Now
Quantum computers can solve some problems that classical computers cannot, especially problems that form the basis for encryption today. For example, Shor's algorithm can break RSA security because it can factor large primes quickly; Grover's algorithm can also threaten symmetric ciphers.
The risk is real, and attackers may be "harvesting" encrypted data today to decrypt later when quantum capabilities develop. The "Harvest Now, Decrypt Later" approach puts sensitive data at risk, including long-term data such as sensitive government records, health information, and intellectual property.
The question for IT and security leaders isn't if it will happen, but when quantum systems will disrupt current security frameworks.
What is Quantum Security?
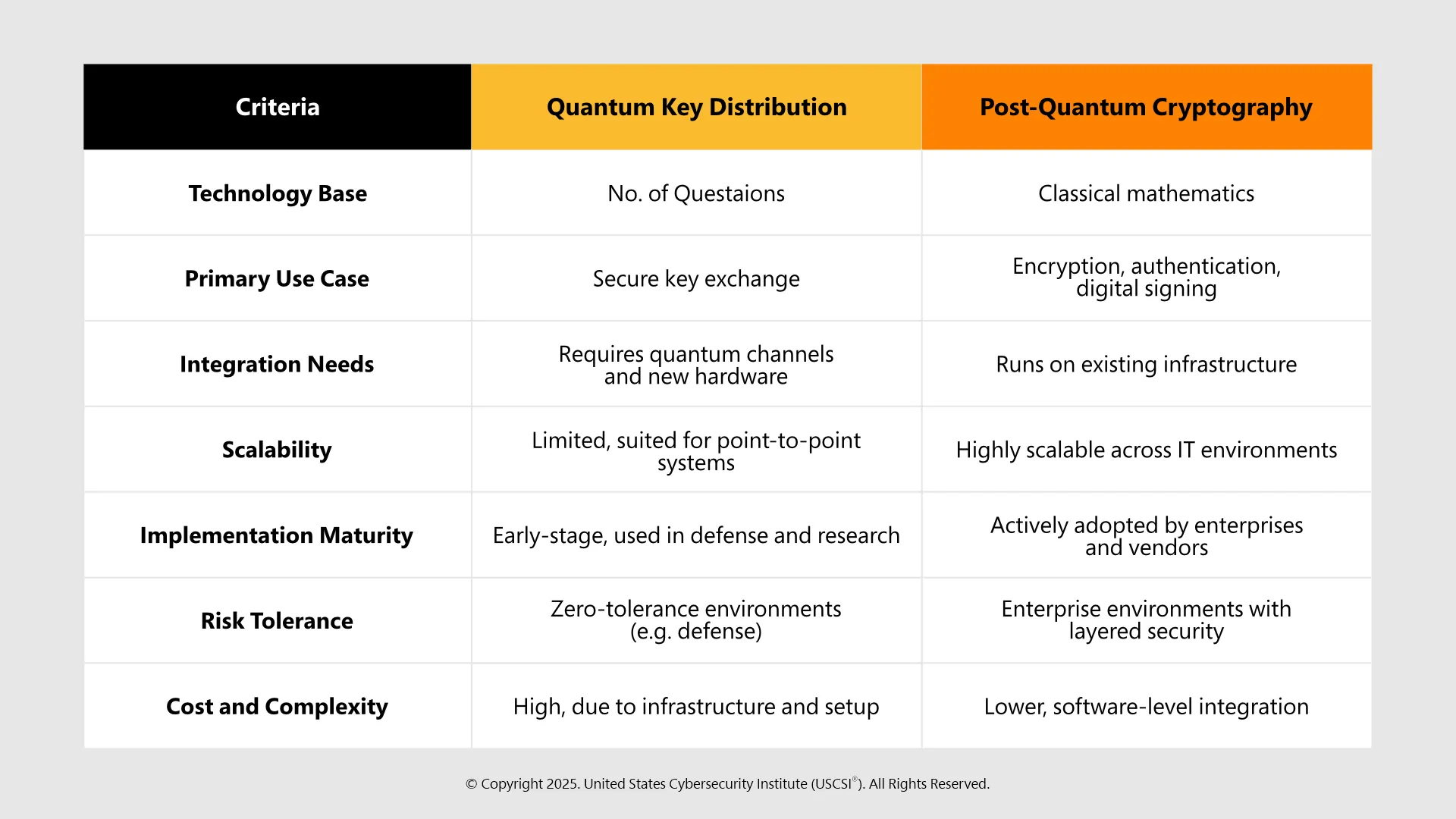
Quantum security refers to the collection of technologies and techniques designed to protect digital systems from quantum computers' higher capabilities. Quantum security provides longer-term data confidentiality and integrity by eliminating vulnerabilities in existing cryptography techniques. Quantum security encompasses two parts: quantum key distribution (QKD) and post-quantum cryptography (PQC), with QKD addressing the threat from a physical perspective and PQC at the algorithmic level.
How Does Quantum Security Work?
Quantum security has two distinct ways of securing assets: Quantum Key Distribution and Post-Quantum Cryptography.
Quantum Key Distribution (QKD):
In the case of QKD, encryption keys are generated and delivered via photons utilizing the principles of quantum mechanics. Because any attempt to intercept the communication will disturb the quantum state of the keys being established, QKD communicates to the two participants that the quantum system has been compromised. QKD demonstrates perfect forward secrecy but requires quantum channels such as fiber or satellites to implement and therefore is not implemented on a large scale in the marketplace.
Post-Quantum Cryptography (PQC):
By contrast, PQC does use classical encryption algorithms that are based on problems that quantum computers cannot solve easily, such as lattice-based, multivariate, and hash-based cryptography. PQC can implement existing networks, servers, and devices, as it does not require new physical infrastructure like QKD; it can be rolled out enterprise-wide.
QKD vs PQC: A Clear Comparison
NIST Standards & Core Algorithms
In response to the quantum threat, the National Institute of Standards and Technology has been developing and approving quantum-safe cryptographic algorithms since 2016.
Your NIST-approved public key post-quantum cryptography algorithm options include:
- Kyber (FIPS 203): A key encapsulation mechanism (KEM) to establish a secure key exchange.
- Dilithium (FIPS 204): A digital signature scheme.
- SPHINCS⁺ (FIPS 205): A hash-based backup signature scheme.
- HQC: An additional backup encryption scheme established in 2025.
These standards provide a foundation for transitioning the world's cybersecurity systems into quantum-safe systems.
Real-World Quantum Security in Action
Quantum security is embraced by tech giants and government entities:
- Toshiba Europe executed QKD over a 254 km fiber infrastructure.
- Fortinet added quantum-safe capabilities to FortiOS for hybrid cryptography.
- Messaging apps like Signal are deploying PQC (Kyber + X25519).
- Countries like India are enhancing quantum-secure networks across research and defense.
These examples demonstrate that quantum security is no longer a matter of the future but is actively shaping IT infrastructures of today.
Key Challenges for CISOs and Cybersecurity Specialists
While urgency exists, organizations are confronting multiple implementation challenges:
- Chief Information Security Officer Tenure vs. Long-Term Approach: Most CISOs will serve 18-24 months, while quantum migration can take years. Strategic continuity is imperative.
- IoT Limitations: Devices, such as smart meters and sensors, have limited memory and may not be capable of processing PQC's challenges.
- Vendor Ecosystem Preparation: Enterprises will need to assess their various vendors for crypto-agility and PQC readiness.
For cybersecurity specialists, this is a wake-up call to skill up and begin preparing for an entirely new threat model.
Roadmap to Quantum-Safe Readiness
Here's how to prepare organizations to safeguard their security:
a) Asset Risk Timeline
Leverage Mosca's Theorem to identify the time to risk for an encrypted piece of data. If it's required to be kept secret for 10+ years, start moving it now.
b) Build Crypto-Agility
Design architecture that can support dynamic upgrades to cryptographic systems without the need to completely redesign the architecture.
c) Collaboration with Vendors
Collaborate with your vendors to verify they comply with NIST PQC standards and know hybrid encryption models.
Training & Certifications for Quantum Security Readiness
As quantum computing pushes traditional cybersecurity boundaries and the need for a trained and certified workforce grows, IT teams, CISOs, and cybersecurity subject matter experts need to get ready to start supporting quantum-safe systems.
Why is Training Important?
Moving towards quantum-safe encryption or crypto-agile infrastructures will require knowledge of NIST approved algorithms, cryptographic risk, and system integration. Organizations that do not provide their workforce training will not be able to keep up with a secure implementation.
Cybersecurity Training Program & Certification Target Areas
- Post-Quantum Cryptography: Practical experience with NIST-approved cryptographic algorithms such as Kyber, Dilithium, and SPHINCS+ for key exchange and digital signatures will prepare participants to include PQC in systems and infrastructure.
- Quantum Key Distribution: Specific training on sharing keys via quantum principles based on entangled particles, which is best suited for high-security organizations.
- AI Integration: Many of the Cybersecurity certifications will include training on the specific use of AI to manage crypto lifecycle, identify protocols that are outdated, and scale adoption of PQC.
- Structured Programs and Certifications: Globally recognized certifications by USCSI provide structured training pathways to cybersecurity specialists with a focus on PQC, migration of cryptography, and quantum-resilient network design.
Curious about how the quantum threat landscape is evolving? Don’t miss the USCSI top predictions for quantum resilience in 2025 to gain strategic foresight and better prepare your cybersecurity roadmap.
Future Trends-Where AI Meets Quantum Security
AI in cybersecurity is proving invaluable for quantum transitions to manage the lifecycle of:
- Automatically detecting obsolete cryptographic protocols
- Automatically enforcing security policies in hybrid systems
- Scaling up PQC deployment in large organizational infrastructures
Organizations can stay agile and compliant with AI-enabled cybersecurity during the transition to quantum.
Conclusion
Quantum security is becoming the foundation of modern cybersecurity. As traditional encryption is becoming increasingly more ineffective against new threats, the focus is on deploying Post-Quantum Cryptography and Quantum Key Distribution in production among enterprise systems.
For cybersecurity leaders, priorities are clear: adopt quantum-safe protocols, enable crypto agility, and invest in reskilling the workforce to keep the threat at a distance. The future quantum era is coming, so it's best to begin preparations now to result in longer-term security.





