

What is an API and How to Implement API Security?
APIs or Application Programming Interfaces are the core element in how modern digital systems communicate, integrate, and deliver value. Be it a mobile banking app communicating with a backend server, cloud services exchanging data, or a third-party developer integrating with e-commerce platforms, an API is a great tool to consider.
With the explosion in use and integration of API across environments, the need for securing these connections has never been greater than today. In this article, let us understand in detail what APIs are, why they are important, and how enterprises can implement strong API security using best practices and real-world techniques to secure their connections and communications.
What is an API?
An API or Application Programming Interface is a set of rules and protocols that helps a software application to communicate with another. It defines how requests should be made, what kinds of responses a user can expect, and the formats used to exchange data or trigger actions. In short, an API acts as a bridge between different applications so that they can work together without sharing important internal details.
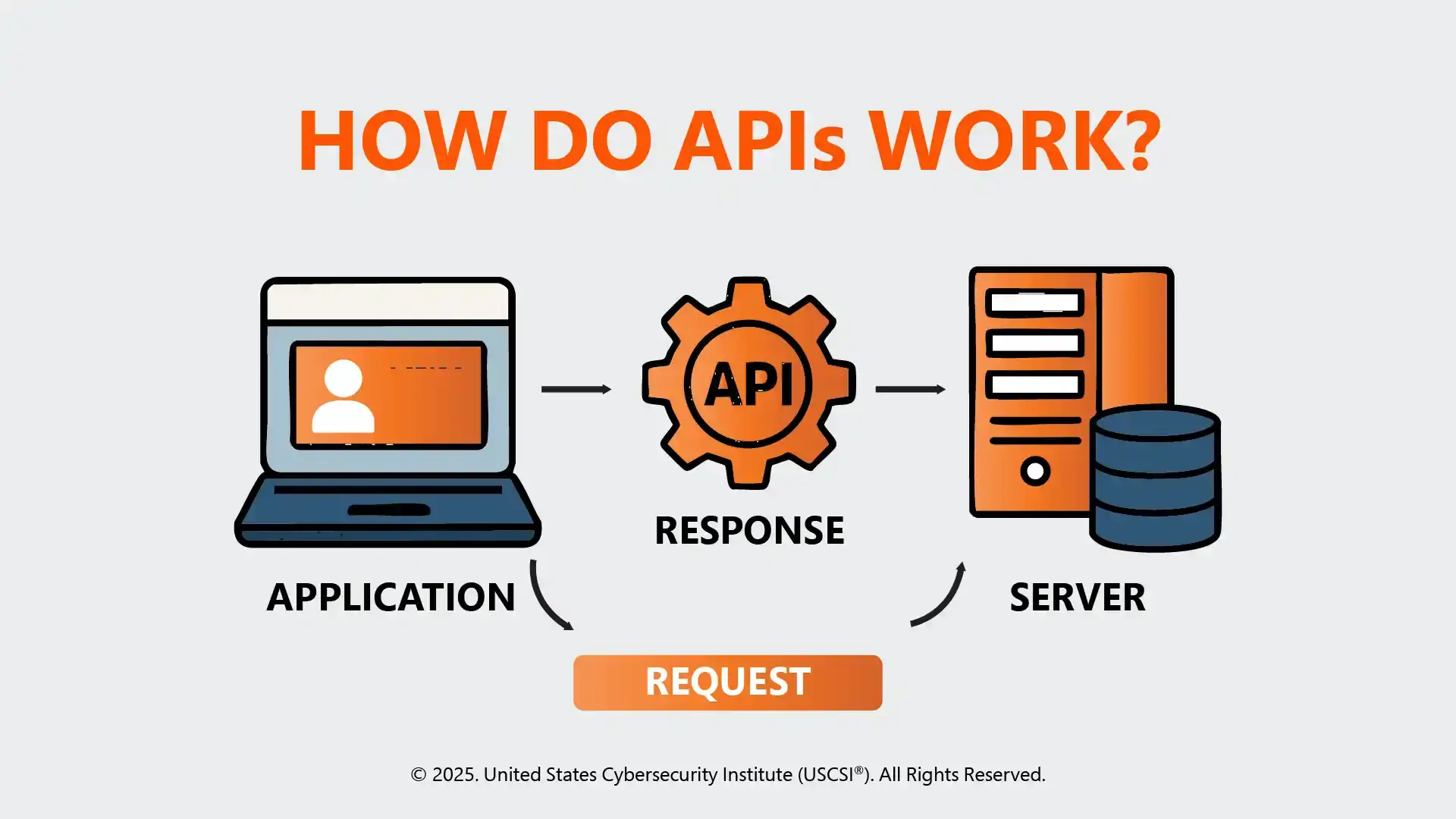
Here’s a simple analogy:
Think of an API as a waiter in a restaurant. You (the client) tell the waiter (API) your order (API request). The waiter then communicates it to the kitchen (server) and then delivers your meal (API response). So, you don’t need to know how the kitchen works internally; you just need to know what to ask for (and how).
Understanding APIs in Brief
What are the core characteristics of APIs?
- Standardized structure – it defines how requests and responses should be formatted
- Interoperability – it helps apps work together even if they are built on different languages and platforms
- Reusability – API developers can reuse existing functionality instead of building it from scratch
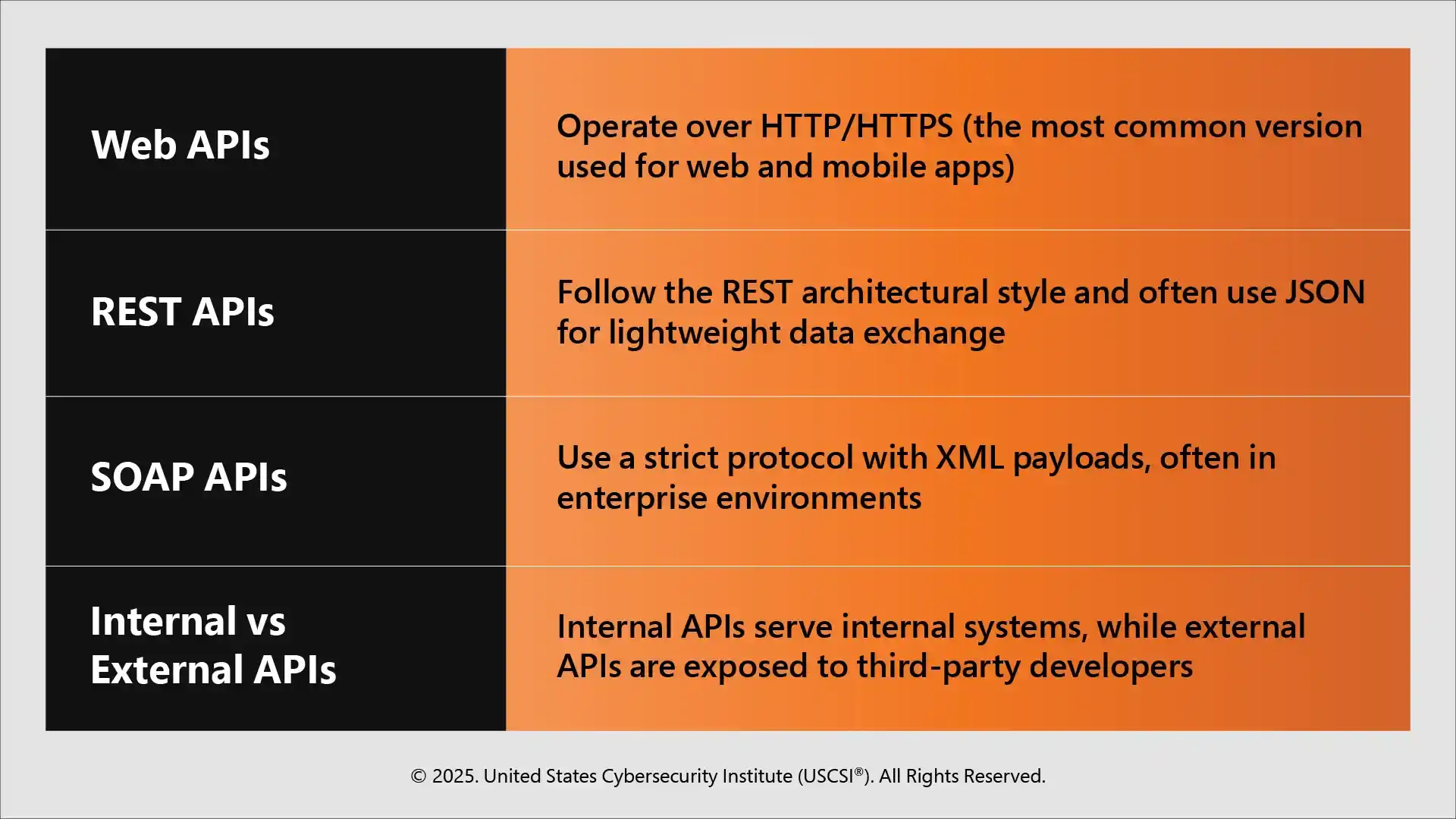
Types of APIs
Depending upon how they communicate, APIs can be of various types, such as:
Why is API Security Important?
Did you know, 57% of organizations experienced at least one API-related data breach in the past two years, highlighting APIs as a major attack vector. Not just that, Among organizations that suffered breaches, 73% reported three or more API-related breaches, indicating repeated exploitation rather than isolated incidents. (Source: Traceable 2025 Global State of API Security)
Enterprises must be aware of the importance of API security as it is essential to ensure safe and secure communication between software/applications.
- APIs can expose important business logic and sensitive data to users
- Insecure APIs often lead to data breaches, financial losses, and reputational damage
- API threats are very common as cybercriminals consider these prime and easy targets for attacks like data scraping or DDoS
- Strong API security strategies can help with proper authentication and authorization for users and systems
- API security also helps protect customer data and comply with privacy and security standards and regulations
- Most importantly, secured APIs prevent abuse, misuse, and disruption in services.
According to Fortune Market Insights, the API Security Market is expected to reach $2.36 billion by 2028.
Organizations must always consider efficient API security tools and API security solutions to keep their assets and data secure from various kinds of emerging and evolving threats that we will discuss in the next section.
What are Common API Security Threats?
Great connectivity also demands great responsibility. APIs can expose important data and functionality to internal teams, partners, and external developers, which can make them a target for attackers if not secured properly.
Below are some of the common API security risks developers should be aware of:
- Unauthorized access – cybercriminals can gain access if there is weak authentication
- Data exposure – APIs can also return too much data or make important data unintentionally visible.
- Injection attacks – this exploits flaws in how input is processed, such as SQL injection
- Denial of service (DoS/DDoS) – this refers to overwhelming the API with a huge number of requests, which makes it unavailable for legitimate/genuine requests
- Broken object-level authorization (BOLA) – in this, attackers exploit how objects are accessed through APIs to gain access to unauthorized data
If not addressed properly, these API security threats can lead to data leaks, data/system breaches, and cause huge reputational damage to organizations, along with legal consequences for compliance violations.
How to Implement API Security – Step-by-step
Most of the cybersecurity frameworks provide clear guidelines for securing data and infrastructure and how to implement various security measures, including those of APIs. In our recent article, TOP 10 IT SECURITY FRAMEWORKS AND STANDARDS TO WATCH IN 2026, you can find the best cybersecurity frameworks to enhance your organization’s overall security posture, including API.
Enterprises looking to implement API security have multiple techniques in option that require a layered as well as defense-in-depth strategy that can secure the entire API lifecycle, from design to runtime.
Here are a few steps to follow:
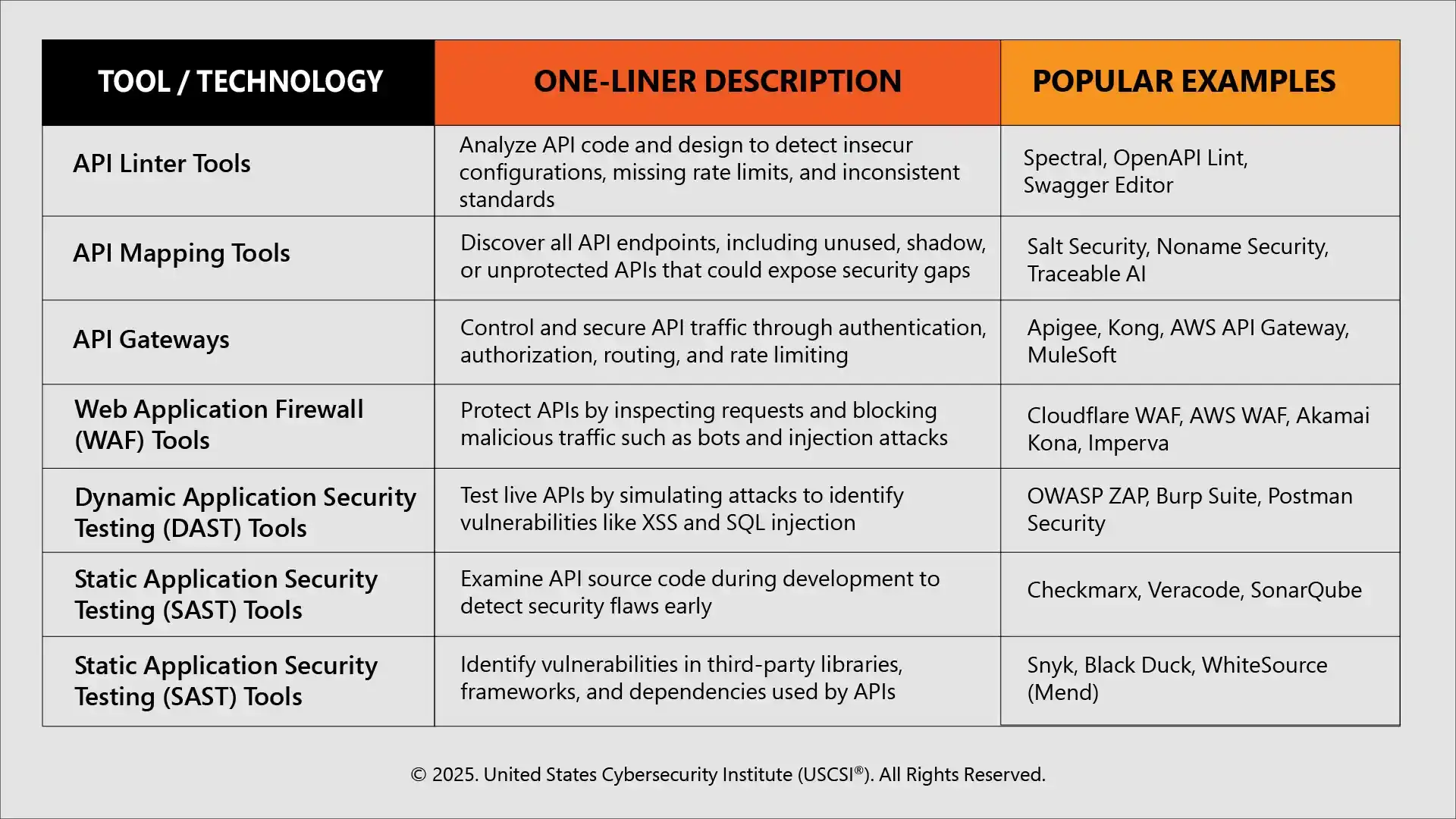
Important Tools and Technologies for API Security
- Secure API Design
Before writing code, establish strong API design principles:
- Use HTTPS everywhere to encrypt all API traffic in transit using protocols like TLS
- Apply the least privilege principle, where you limit API access strictly to only what’s needed
- Use API specifications, for example, OpenAPI, that define clear expectations for API behavior
- Authentication and Authorization
Authentication and authorization are the foundational control methods in an API security strategy.
- Authentication – it verifies who is calling the API (API keys, OAuth 2.0 tokens, JWTs)
- Authorization – it determines what the authenticated user can do (like role-based access control)
Mutual TLS (mTLS) helps check if both client and server are authenticated using certificates and thus helps provide greater protection.
Note: Avoid just passing API keys in plaintext. Always combine them with TLS encryption to prevent interception.
- Input validation and schema enforcement
APIs should strictly validate incoming data against an expected schema. Accept only expected parameters and reject malformed requests. This helps prevent injection attacks and unexpected behavior.
- Rate Limiting and Throttling
Control the frequency of API calls to protect against abuse. This includes:
- Rate limiting – caps the number of requests per user or IP for a given timeframe
- Throttling – makes traffic bursts smooth to preserve system performance and uptime
These methods are useful for APIs that are exposed publicly on the internet.
- API Gateways and Security Layer
An API gateway centralizes several important security functions, such as:
- Authentication & authorization
- Traffic routing
- Logging and monitoring
- Rate limiting and throttling
- Protocol translation
These gateways serve as the control plane between external traffic and backend services. They add a protective barrier against various API threats.
- Encryption
It is recommended to encrypt sensitive data, such as tokens or credentials, at rest. Beyond HTTPS, using strong cryptographic standards and managing encryption keys securely will be helpful.
Apart from these, enterprises can also use advanced API security tools for logging, monitoring, analytics, and testing the security.
Important Tools and Technologies for API Security
To sum up!
APIs are the backbone of modern digital applications. However, they bring in a lot of security risks if left unprotected. By implementing a layered API security strategy that covers secure design, testing, monitoring, and specialized API security tools, enterprises can prevent data breaches and service abuse. Integrating API security throughout the development lifecycle can help businesses with safe innovation, protect sensitive data, and maintain trust in an ever-expanding digital ecosystem.
With the best cybersecurity certifications from USCSI®, professionals can learn how to design, implement, and monitor effective API security strategies and tools. These online self-paced programs won’t just help you grow in your career but also ensure you have the relevant skills and knowledge to stay competitive in the evolving cybersecurity job market.





